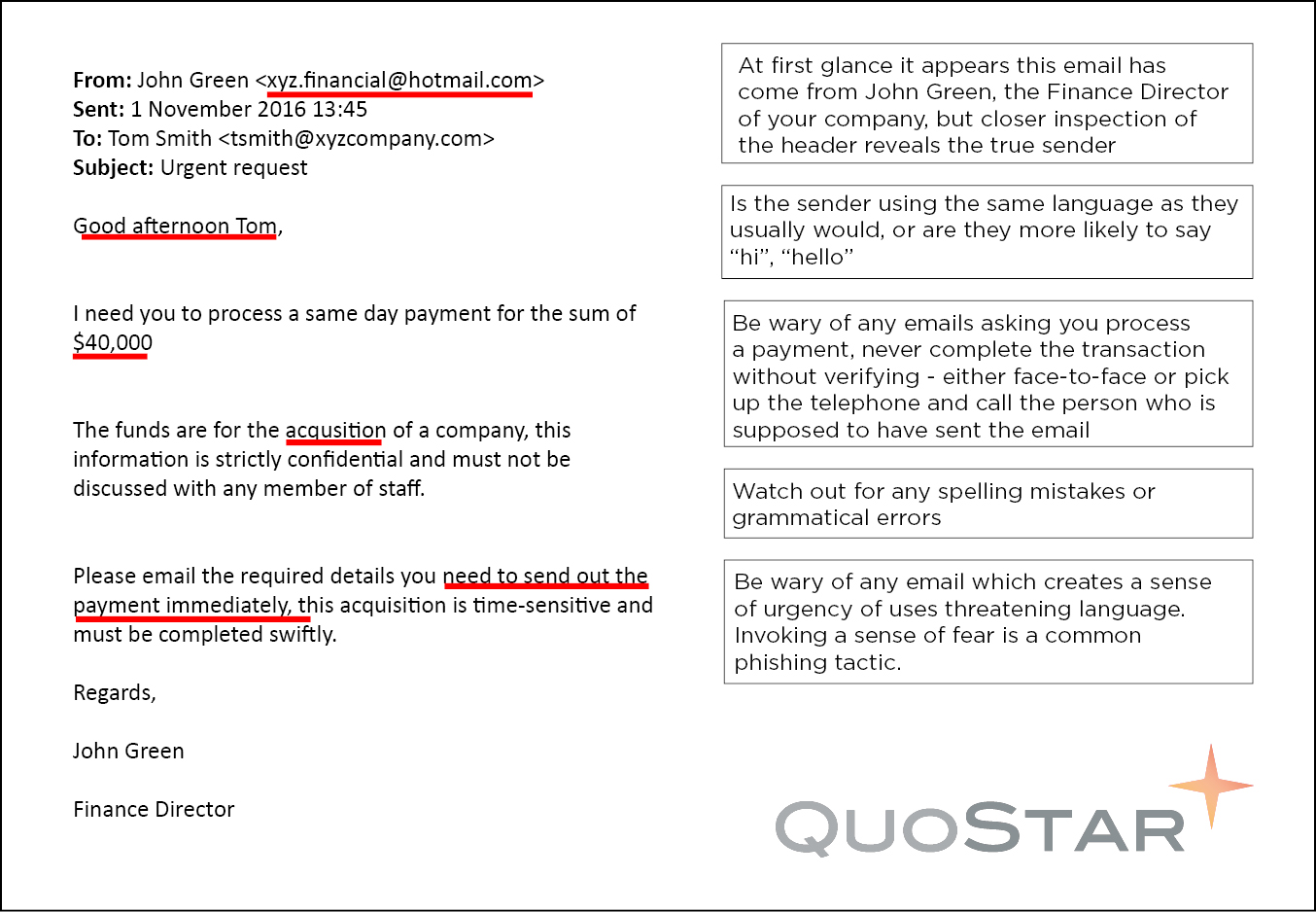
It’s been mere weeks since the outbreak of WannaCry, a global ransomware attack which left many organisations’ IT infrastructure in lockdown, but this week companies worldwide are again reporting that they have been struck by another major global cyber attack.

What happened?
Late on Monday night, the first reports surfaced of another global cyber attack. This time the attack began in Ukraine and appears to have spread through a hacked Ukrainian accountancy software developer to companies in Russia, Western Europe, the US and Australia.
Around 2,000 individuals and organisations worldwide have reportedly been affected. The list includes advertising firm WPP, food company Mondelez, legal firm DLA Piper and Danish shipping and transport firm Maersk.
Infected computers displayed a screen warning users that their files were encrypted and no longer accessible. A $300 ransom, paid in Bitcoin, was demanded to release the decryption key.
How did it happen?
Initially, it was believed this outbreak was a new version of “Petya” – ransomware that emerged last year. But in the hours after the outbreak security researchers noticed that the resemblance between Petya and this malware was only “skin deep”.
Kaspersky Lab reported that they believed this malware to be “new” and dubbed it “NotPetya”, a tongue-in-cheek name based on the fact that both outbreaks share a similar amount of code. Others have also referred to the outbreak as “Petna”, “Pneytna” and “Goldeneye”.
Worryingly experts are suggesting that this latest outbreak of malware is taking advantage of the same weaknesses used by the WannaCry attack last month. Like WannaCry, “NotPetya” utilises the EternalBlue vulnerability in Microsoft Windows to move through the network, infecting other machines and systems as it goes by injecting malicious code into them. However, unlike WannaCry it does not contain the code which enables it to leave the network once it has spread.
Microsoft did release a patch for this vulnerability, even for operating systems which were no longer under support – which is incredibly rare in itself – this latest attack suggests that many companies did not apply it. Security experts have said this is partly because WannaCry was tackled so quickly, but also because industrial firms struggle to apply software patches quickly as their systems cannot have downtime.
The motive of malware
Now the dust is beginning to settle and there’s been time to analyse Tuesday’s outbreak it’s been suggested that although “NotPetya” bears all the hallmarks of ransomware it, in fact, has a much more sinister motive – to permanently destroy data.
By its very definition ransomware is designed to make money by holding data hostage. Only releasing data once the victim pays the fee. Yet with “NotPetya” there’s very little money to be found. One security researcher, who goes by the handle “the grugq“, states that “the malware’s advanced intrusion techniques is in stark contrast to its rudimentary payment structure”. Some of the elements researchers have flagged include:
- Designed to overwrite the master boot record, meaning even with a decryption key it would be impossible to restore disks.
- The ransom note does not display a “personal infection ID” which attackers need to decrypt a paying user’s computer.
- Used a single bitcoin address to receive bitcoin payments.
- Required victims to manually type a long string of human-unfriendly characters into an email address. This is typically avoided as it decreases the likelihood of payment.
There have been differing opinions on the motive behind “NotPetya”. Some researchers speculate that it looks like a “state-sponsored” or a “state operating through proxy” attack. This is due to the fact that the infection seems to specifically target Ukraine’s vital institutions, such as its central bank, airport and metro transport, rather than focusing on more lucrative targets.
Another suggestion is that Tuesday’s attack was “a lure to control the media narrative, especially after the WannaCry incidents to attract attention to some mysterious hacker group”.
The future of global cyber attacks
As society becomes increasingly connected and ever more reliant on technology, this wave of global cyber-attacks raises questions about the future for businesses.
Traditionally you would have people who would hack for “fun”, just to prove that they could enter a company’s systems. Now the majority of today’s hackers are looking for financial gain. Using the threat of locked-down systems or the release of sensitive data to extort payment from a business. However, if we are entering an era whereby businesses are attacked simply to cause the maximum damage possible then it is right to be concerned.
Businesses sometimes decide to pay ransomware demands, simply because it costs less than losing a day’s productivity. Even if they dislike the idea of responding to ransom demands. However, if you now have malware which simply poses as ransomware, it changes things. In this case, even if a company responds to the demands it won’t guarantee the return of their files and, depending on their policies, who knows how much data could be permanently destroyed.
There is no doubt that “NotPetya” was a sophisticated piece of malware, designed to “spread fast and cause damage with a plausibly deniable cover of ransomware”. Which raises questions about potential attacks in the future and the motives behind them, e.g. cyberterrorism, revenge, geopolitics etc.
What, if anything, can you do?
Although the increase in cyber-attacks, and their global reach, is concerning, there are steps businesses can take.
On a day-to-day level, you should ensure that all your systems and software remain up to date. Apply the latest patches when they are released and ensure you’re running up to date Anti-Virus and Firewall solutions. Staff training also plays an important role. With email and social engineering popular attack methods, it’s vital that they recognise potential threats and know how to respond.
Backups are critical, but they need to organised in a particular way to be “ransomware-proof”. A three-tier approach, which comprises short, medium and long-term backups, is a more reliable way to protect your data:
- Short-Term – Constant backups of files through a file/block-level replication service. Or on your own network but with proprietary protocols so the backup isn’t visible to attackers.
- Medium Term – Regular backups onto easily accessible storage devices logically isolated from the rest of the network
- Long-Term – Offline, encrypted storage, physically isolated from the rest of your company and users. These backups are less frequent and comprehensive but are there in the case of an emergency.
Alongside this, you should also run regular tests of your backups to ensure all is working as it should be. Regularly scan for malware in case ransomware enters the systems and hides in encrypted files when they are backed up. This will help prevent users from becoming stuck in a continual loop of backup-restore-encrypt.
Those businesses who are particularly reliant on certain systems, who deal with large quantities of sensitive information or have access to significant funds may want to go further and consider advanced security solutions.







 According to recent surveys, the Financial Services sector suffered
According to recent surveys, the Financial Services sector suffered 
