Having a CIO-level professional on your board is the first step to treating IT as a strategic asset rather than a cost. Question is, full time, interim or virtual CIO?
IT is no different from any other business-critical area. You know a transformational IT roadmap will bring significant operational and financial benefits, but you need a professional with the right skillset to pull it all together. It needs a strategy, leadership, and ongoing management if you want to achieve measurable returns and competitive advantage. A CIO – but do you need that position filled in-house or with a virtual CIO?
A CIO (Chief Information Officer) is usually the most senior technology executive inside a business. They hold responsibility for the IT strategy and determine areas for improvement and development within the IT systems and processes. A commercial mindset, extensive experience as well as a deep understanding experience of technology and its application, is necessary for a CIO.
A CIO will focus on IT strategy and leadership, ensuring that IT is aligned with business goals.
Unlike an IT Manager, a CIO is more outward-facing. They will focus on IT strategy and leadership, ensuring that IT is aligned with business goals and works in unison with the overall business strategy. However, as the CIO is often the executive level interface between the IT department and the rest of the business, they need to keep abreast of day-to-day operations and issues. Any IT projects will likely be owned by the CIO, and they will be accountable for signing off on the solution and the implementation. They will ultimately be responsible for the project’s success, outcomes, and ultimately the ROI. A good CIO can see past emerging technology hype.
Many businesses assume that the only way to gain access to a CIO’s knowledge and experience is a permanent hire. While this is certainly one option, it can be costly and unnecessary for your current needs. If you’re flying blind how will you know they really are as experienced in the field as you require? There are alternatives available that may be a better fit for you.
We explore four different ways businesses can fill the CIO role: Full-time Permanent CIO, Interim CIO, Virtual CIO and a CIO service. We look at pros and cons of each to help you with the decision-making process.
The 4 types of CIO you could hire
- Full-time, permanent CIO
A full time permanent hire CIO is an experienced technology leader who sits within the business at board level, with full time generally meaning 40+ hour week for most – and doesn’t come cheap.
What are the benefits of hiring a full-time CIO?
- Dedicated and experienced IT leadership at board level
- Effective IT strategy that works in unison with the business strategy
- Removes the load from senior leadership, allowing focus on their expert areas of the business
- Delivery of operational improvements and a measurable return – they’ll advise on the right investments
- Significantly reduces the likelihood of poor project outcomes, disruption and disgruntled staff.
- Enables businesses to address and manage risk more effectively
- Awareness of evolving threats, as well as changes in the commercial landscape
- Gives a competitive edge, allowing the business to mitigate risk and capitalise on opportunities their competitors may be unaware of.
What are the disadvantages of hiring a full-time CIO?
- The CIO skillset is in high demand – these senior professionals can pick and choose their roles to some extent
- The specialist knowledge makes a CIO an expensive hire. (Average salaries are around £141,000 but can be upwards of £200,000)
- If this is the first CIO a business has hired, then senior leadership may be unsure of what they need.
- Difficulties assessing candidates’ experience and whether it aligns with business needs only serve to make the process even longer
- Mid-market businesses may not have the requirements for a full-time CIO
- Although the strategic direction and commercial focus will undoubtedly be of benefit, a less complex IT environment and a lower capacity for projects could mean a limited scope for change
- Research shows that CIO tenures are short, with an average of just 4.3 years – making them the shortest-tenured C-suite exec
- Two-year stints aren’t uncommon as CIOs often want new challenges and the opportunity to deliver real change.
- A full-time CIO may turn out to be a very expensive, short-term hire. You might find yourself stuck in what feels like a constant recruitment cycle.
- Interim CIO
Also known as a Contract CIO, an Interim CIO is an experienced technology leader who temporarily fills the CIO role. The average tenure is between six months to two years and an Interim CIO is usually bought in to tackle a specific challenge while the business transitions between permanent CIOs. However, they are also sometimes hired to support and mentor a newly hired or promoted CIO.
An Interim CIO’s role typically falls into one of two camps:
- Responsible for building corporate resilience so the business can maintain a competitive advantage. Essentially keeping the lights on.
- A transformational role, tasked with formulating a strategic plan and executing it.
What are the benefits of an Interim CIO?
- Quicker to hire – a benefit for businesses in ‘crisis mode’ who cannot afford to wait to make a permanent hire
- A benefit to time-sensitive projects (such as an M&A) and need for immediate access to the skillset
- Their laser focus on a specific project or business area allows Interim CIOs to add immediate value
- A dedicated, experienced professional driving an initiative increases the likelihood of that project remaining on track and delivering expected outcomes
- A rich and varied CV can make Interim CIOs valuable mentors
- Experience across multiple industries, business types and environments. They will have seen a multitude of scenarios and challenges – knowledge that can aid the IT department
- Can help senior leadership make better IT-related decisions
What are the disadvantages of an Interim CIO?
- Interim CIOs are an expensive hire
- They are in high demand, and with a limited number of professionals available, they can cherry-pick their projects
- An Interim CIO is only going to be available for a set period, so there may be limits as to what can be accomplished in that time
- Businesses will need to define a clear objective for the engagement and a fixed schedule for delivery
- Existing problems in the business environment may affect the success of delivery
- Long-term or chronic underinvestment in the IT environment, problems left behind by predecessors, or a need for overall business transformation can all affect project delivery
- An Interim CIO will need to quickly get up to speed with the organisation structure and technology portfolio, and quickly win round and influence key team members to ensure objectives are met. (of course, it’s not impossible, but the senior leadership team need to be confident in their hire).
- Virtual CIO
A Virtual CIO (vCIO), also known as a fractional CIO, provides consultation on IT and technology strategy as a third party. Compared to full-time and Interim CIOs, who take an active role in company operations, the vCIO is often an advisory role.
They will have similar responsibilities to an in-house CIO, but the core difference is that the service is delivered virtually. You may not meet your Virtual CIO and there could be multiple people working on the business at different times, depending on the structure of service.
What are the benefits of a Virtual CIO?
- A vCIO Service offers significant cost savings compared to hiring internally
- Most services are offered at an hourly rate or flat fee, making it easy to budget and account for
- With a vCIO you will have someone dedicated to strategic IT management, even if it’s on a limited basis
- A good starting point for companies new to the strategic approach
- Will be better than people within the business spending a few hours here and there trying to make improvements.
What are the disadvantages of a Virtual CIO?
- Virtual CIO Services focus more on the improvement of day-to-day operations, rather than long-term strategic planning, management and innovation
- A vCIO typically works across multiple businesses, so may not be as readily available to deal with issues that arise
- Businesses which are tech-heavy or very reliant on technology will probably need a more heavyweight and involved resource
- As a virtual service, you may have little to no ‘face time’ with your CIO
- It may be difficult to build trust as the CIO may feel disconnected from the business, affecting results delivery
- Depending on the provider you have chosen, you may also need to factor in time zone and cultural differences.
- The CIO Service – a better alternative for the mid-market…
You may feel that a virtual CIO wont deliver the expertise and attention needed to achieve measurable outcomes – but you also don’t have the resources or requirements to justify a full-time hire, and an interim CIO just won’t do.
Often, it’s not operationally or commercially viable for mid-sized organisations to have a full-time senior internal IT professional. However, access to professional IT management expertise and skills offers a competitive advantage. With the right management, IT can improve the business’s bottom line, aid client engagement and service delivery, and improve staff retention.
Luckily there is a fourth alternative that bridges the gap, while still delivering tangible value on a cost-effective and flexible basis – a CIO Service.
QuoStar’s CIO Service has been specifically designed to provide mid-market businesses with the strategic IT leadership necessary to deliver the benefits of a full-time CIO but without the significant costs.
What are the benefits of a CIO Service?
- Harness the transformational potential of IT
- Enables access to the skills, expertise and commercial acumen of a CIO-level consultant
- Flexible and cost-efficient
- Supports organisations throughout their entire IT transformation journey; from evaluating current standing and areas for improvement, through to building and implementing a roadmap and change plans.
Our QuoStar CIO Service offers:
- Proven, seasoned sector-specific CIOs with a combined 60+ years’ experience
- A proven methodology and framework to deliver a strategy and transformation
- Completely embedded within your organisation – one of the team
- Guaranteed results backed by our Outcome Assured™ promise
- Delivering measurable outcomes for businesses just like yours!
In 2021, experts estimate there will be a cyber-attack incident every 11 seconds.
That’s twice what it was in 2019.
And four times the rate five years ago.
These shocking statistics probably aren’t even that shocking. Every Director knows that security is a pressing issue. It’s a topic of conversation in every board room and a significant budget has been allocated to invest in various security measures and solutions.
However, there’s a weak link in the business which is often overlooked. Your employees. While they might not mean to put the business at risk, their actions can do just that.
From clicking on links in phishing emails and actioning fraudulent bank transfer requests, through to connecting to insecure Wi-Fi networks and sharing personal data incorrectly. All these actions can result in a breach or successful attack, causing financial and reputational damage.
Most employees are not malicious, they simply are not aware of the risks. They don’t understand that they are a target, and they don’t know how to spot the danger signs. Many don’t understand that security is their personal responsibility and even fewer understand sensitive data privacy best practices. Thankfully, this can be easily addressed with effective security awareness training. In this article, we will cover the benefits and types of security awareness training, as well as best practice tips to follow for an effective program.
What is security awareness training?
Security awareness training is designed to educate employees about the important role they play in helping prevent information breaches. It provides formal education about the type of risks facing the businesses, how employees might interact with them or be targeted by them, and how their actions can have a positive or negative affect.
‘Real-life’ scenarios – for example, demonstrating how their response to a phishing email could cost the business thousands of pounds – are often included to drive the message home and show the employee what a breach would feel like.
Quizzes, questionnaires, and games can also be used to test employees’ knowledge post-training and identify any weak spots. There are also various online systems that train and test employees in an automated manner, flagging those users who need additional focus and training.
Why is security awareness training important?
Security awareness training ensures everyone in the business is aware of the threats and how they might present themselves. It helps build a security-aware culture and encourages everyone to follow best practice. For example, instead of the accounts department immediately actioning a bank transfer due to an email from the Financial Director, they know to double-check the request with another method (e.g., a call, a Teams message).
A more security-aware culture will significantly reduce the chance of a successful attack against your business. Research found that security awareness training could reduce the threat of socially engineered cyber threats by up to 70%
Training is also a requirement for compliance purposes in certain industries. The Financial Conduct Authority (FCA) states:
“Firms of all sizes need to develop a ‘security culture’, from the board down to every employee. Firms should be able to identify and prioritise their information assets – hardware, software, and people. They should protect these assets, detect breaches, respond to and recover from incidents, and constantly evolve to meet new threats.”
Types of security awareness training
- Phishing – Trains employees on how to recognise potential phishing messages by demonstrating what could happen if they respond to one.
- Passwords – Promotes password best practice, ensuring strong passwords are created and are not used across multiple accounts or shared with others.
- Privacy PII – Shows employees how to protect personal information in the business, including clients, prospects, colleagues, and partners.
- PCI Compliance – This training is required to comply with the PCI DSS (Requirement 12.6). Educates staff on the requirements, roles and processes and demonstrates the severe financial and reputational damage of a payment card data breach. Reinforces best practice to help staff actively keep card data safe and reduce the likelihood of a breach.
- Ransomware – Demonstrate to employees just how easy it is to be attacked and the destructive consequences.
- CEO/Wire Fraud – Fraudulent emails designed to trick the employee to think they are responding to the CEO (or another senior executive), which shows them how easy it is to be conned. Helps employees to recognise the first signs of risk and encourages the practice of double-checking when unsure how genuine a request is.
- Data in Motion – Teaches employees data security best practices to ensure vulnerable data is not put at risk. Highlights the dangers of behaviours such as sending company attachments to home email accounts, copying company data to personal cloud storage, plugging ‘found’ USB drives into company devices
- Office Hygiene – Educate employees on the importance of physical security, demonstrating the risk of unsecured paper, unlocked screens, open buildings and more.
- GDPR – Ensure all employees are aware and understand data privacy rights – and the severe penalties for breach or non-compliance.
- Social Engineering – Train employees on the various methods and guises hackers may use to gain illegal access to their computer, including phone, email, mail or direct contact.
How often should train employees?
Ideally, every four to six months. There are various software solutions that test and train users more frequently than this, perhaps weekly, however they do not cover all areas of cyber-security.
Research found that after four months, employees were easily able to spot phishing emails but after six, they began to forget the learning. Although this research was specifically about identifying phishing emails, it can be applied to all types of security awareness training.
However, it is up to you to determine the right cadence. Use this timeframe as a starting point. In the beginning, you may need to test employees more frequently.
The key is to strike the right balance. Employees need to be informed and educated, but you want them to be proactively engaged. Training that occurs too frequently risks becoming a chore and treated as a tick box exercise. Employees rush to get it done, rather than engage with the learning, as they know they will have to do it again in a few weeks.
How expensive is security awareness training?
The cost of security awareness training will largely depend on the provider, the type of training and the number of employees. Some providers often tiered pricing with different training methods at each tier. As an example, some of the automated training and testing systems for training users, particularly around phishing and ransomware can be in the region of £12 a year per user.
However, with the average cost of a data breach $3.86 million, the cost of your training program will unlikely ever come close to the cost of a successful data breach. In fact, research shows that employees with less than 1,000 employees will see an ROI of 69% from a security training program.
Best practice tips for an effective training program
Effective training needs to deliver the right information, at the right level, at the right time.
1. Repeat, repeat, repeat
Staff will only recall approximately 90% of training after a month. So, a programme of sustained and repeated training is the best way to ensure knowledge retention.
Plus, the cyber-security landscape is rapidly and constantly developing. New threats occur all the time and you need to equip your staff to deal with them.
2. Gamify your training
Mandatory training can seem dull, leading employees to switch off and become disengaged. You need to ensure these important messages are hitting home. Experiential learning through game-like approaches can help some staff members remember things more effectively.
Studies show that using humour and entertainment in the training process boosts engagement. Nearly 60% of employees prefer training which mixes serious and entertaining content.
3. Break training down into manageable chunks
Hours of back-to-back training is unlikely to engage anyone. In fact, your employees will probably just see it as another ‘tick box’ chore – not ideal for building a security-aware culture. Instead, break your training into bite-size chunks, spread out across the year.
4. Try different methods
Employees all have different methods of learning. What suits one may not suit another, so it’s important to switch up training delivery. Posters, books, quizzes, games, interactive demos and small group training are just some of the ways to educate employees. Unfortunately, you can’t just buy an online training and testing package and believe that’s your training box ticked.
5. Cover a range of topics
While phishing is a top attack vector, it’s important that your training does not focus solely on one area. You need to educate your employees on a wide variety of topics, including those which they might not connect directly with the workplace. For example:
- Not to overshare information on social media
- Dangers of public Wi-Fi and how to use it safely
- Not to plug unknown USB devices into corporate devices
- How to manage passwords
If you’ve ever had to request budget from the board or tried to get buy-in for an IT project, you will know how difficult it can be to get the board engaged with IT. Despite the critical role IT plays in operations, too many senior executives still see it solely as a cost to the business rather than as a competitive advantage.
Research shows that regular conversations between IT and the board actually decreases IT and cyber risk, while increasing innovation and IT project ROI. These achievements improve the more frequently the conversations occur. Conversations that occur every quarter hold more value than those held bi-annually or annually.
However, getting these conversations to happen in the first place is often the most difficult part. IT Managers can struggle to get their voice heard at board level and IT often does not feature on the agenda as often as it should. Part of the problem is this often requires a change in culture, but the good news is IT Managers can facilitate this by framing their conversations with the board in the right way.
3 strategies to engage the Board of Directors with IT
Most organisations spend a significant portion of their revenue on their IT, so they need to be sure that it is being invested wisely and delivers a return for the business.
This can only happen when senior executives fully embrace the potential of IT and view it as a strategic asset. While it’s important that IT has a voice at board level, the conversations themselves need to be effective too. We’ve compiled three best practice tips to help IT Managers frame the conversation in a way the board will engage with.

1. Make Technology a Routine Part of Conversation
IT Managers need to think strategically about how they can navigate technology conversations with the board. Assess the levels of technical knowledge and understanding to determine whether an educational component is required and build conversations accordingly.
Some members of the board may be more technologically-savvy or be more. Identify these allies and build relationships with them as they can help you garner support for IT investment and focus from other members of the board.
Consistent communication is key so ensure IT features as standing item on the agenda or designate regular meetings where you can focus solely on IT. Strike the balance between protection and growth and build a narrative which focuses on the short term (6-12 months) and the long-term (5+ years).
Any conversations about long-term strategic planning should be a collaborative effort. IT Managers should be fully briefed on the intended strategic direction of the business so they can educate the board about the relevant risks, opportunities, and industry changes, ensuring the IT strategy supports the business objectives and the budget is allocated effectively.
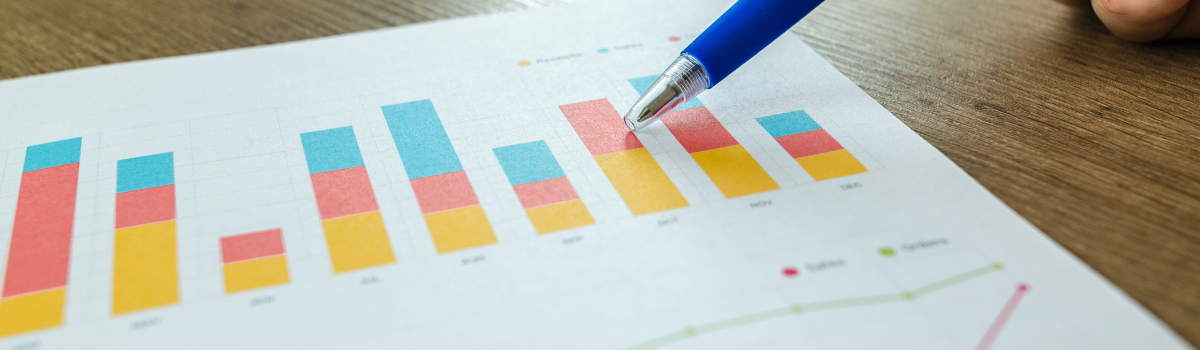
2. Demonstrate the business value of strategic IT investment
You will need to make the case for IT investment, so be prepared to convey the financial, operational and reputational benefits. Back your pitches with data and present the information clearly and concisely e.g., by utilising dashboards and scorecards.
You may need to ‘connect the dots’ and give context to the risks facing the business. If board members do not understand the mitigating effects of benefits a particular solution or service will deliver, they may not be willing to allocate the funds. For example, data security might be a concern for the board, but they may not understand why the business is a target, where they are vulnerable, the effects a successful attack can have and how it can be prevented. Take into context the board’s own appetite for risk and align your recommendations and scorecards to reflect this.
Budgets can vary widely so you may wish to present a shortlist of options to the board. However, if you do decide to do this you need to ensure the board is fully aware of the limitations of each one, so they do not decide based purely on flat costs.

3. Focus the conversation on the right topics
Try not to get bogged down in the technical detail during conversations with the board. It’s unlikely that their level of technical knowledge will match your own, so they will be less likely to engage if it doesn’t seem directly relevant to the business. Instead, focus the conversations on the potential impact and deliverables of IT.
Performance
Ensure that the board understand how IT can positively or negatively impact the performance of the business.
- Financial – Link technology investments to financial performance such as profitability, margin and revenue. Demonstrating the positive impact can help the board see IT as more than an operational cost.
- Operational – Demonstrate how IT can improve the efficiency of operations and free up budget for innovation and business transformation. This may include things like automating processes, replacing legacy systems, and embracing cloud services. IT Managers can support this process by measuring, reporting, and discussing the impact of technology-driven business transformation.
Risk
Ensure the board keeps up to date with current and emerging threats, be it cyber-attacks or disruptive technologies. IT Managers can help develop the risk appetite and measures to prevent unnecessary risks from being taken. IT and Business must be wholly aligned on risk appetite levels to ensure neither side make inappropriate risk management decisions.
- Cyber Risk – Businesses must be able to protect their assets from cyber-attacks if they want to achieve strategic goals. IT Managers have the responsibility to educate the board on current and emerging risks, the potential threat to the business and remedial actions.
- Regulations – Technology can help businesses comply with regulations, but it also the subject of regulations itself – such as data privacy. Boards need to be aware of how technology can speed the process of meeting compliance policies, as well as where regulations may require additional investment or affect company priorities. Conversations should focus on the positive and negative implications of the regulations, the opportunities for rationalisation and any other business impacts.
- Industry Challenges – New technologies can topple a company’s competitive position and business models. Help board members understand the risks and opportunities of technology-driven industry disruption to ensure the business doesn’t fall behind.
Strategy
IT Managers should help guide the overall business strategy by educating board members on the strategic potential of IT and other disruptive technologies
- Innovation – IT Managers can help create a bolder risk appetite by demonstrating how the effective use of technology can result in business growth. Successful innovation requires a culture of continual incremental improvements. Boards need to give IT Manager the opportunities to test, experiment and analyse.
- Data – Help the board understand how technologies such as machine learning, natural language engines and AI, can help businesses better collect, process, and analyse customer data. Highlight how this data be used for more effective decision making and monetised for business success.
- Client Experience – Customer demands are constantly changing and increasing. Businesses need to keep pace with this is they want to both attract new customer and retain their existing ones. Service levels are a key battleground. As service levels increase across all industries, tolerance levels have declined, and customers are no longer prepared to accept reduced levels out of brand loyalty. IT Managers can help the board meet these challenges by showing how to leverage technology to proactively anticipate and address customer needs. These conversations can help ensure the pace of technology change aligns with customer readiness.
Strategic development for IT Managers
IT Managers have a huge wealth of technical experience and understanding, so it makes sense why they are often heavily focused on the technical details.
This knowledge is highly valuable to a business, but it doesn’t always translate to the board. If they do not understand, they will not engage. They need to see the business benefits of investing in IT. Requesting budget to replace an old server, for example, is not enough. However, if you explain that the new server will help increase resilience, availability, and network performance, and enable employees to deliver faster customer service, the board can begin to understand the ROI of that investment.
If you’re used to focusing on the technical details, then framing conversations in this way can feel a little uncomfortable initially. IT Managers who want to take a more strategic standpoint should seek out additional training and mentorship from experienced CIOs and IT Consultants. A dedicated Coach can give IT Managers advice and direction, provide education (where required), share knowledge and best practice, help develop a commercial mindset, and talk through challenges faced by the business and how to overcome them.
What are the essential cyber-security measures every business needs?
In today’s digital era, advancements in technology are happening very rapidly. Therefore our defence systems against very real cyber-security threats must keep pace. If the correct measures aren’t taken, your business might be more at risk than you think. Here are 9 essential cyber-security measures your business can take.
Are you relying on the same security basics you were a few years ago?
It’s easy for time to pass unnoticed while all these advancements happen around us. Before you know it, you’re relying on the same old security basics to protect your business as you were a few years ago – firewalls, antivirus and intrusion detection software. Most people update their mobile phone software more frequently than that. So here are our 9 recommendations on how to keep your company more secure.
Why is it so important?
The truth is, we all feel impervious to cyber-crime and security breaches. It’s just something that happens to other people – until one day it’s not. Even if a direct financial attack is not a concern for a business because that’s locked down, many people are unaware of the intrinsic value of the data their business holds in today’s world.
Hackers aren’t just after your bank accounts.
Cyber-crime is now an industry that produces over £1 trillion in revenue for cyber-criminals. Ransomware can be used to encrypt a company’s files and hold them for ransom. Network penetration can enable mass data theft and crypto-jacking to harvest crypto-currencies by stealing your machine’s processing power. Money can even be gained by using social engineering to persuade employees to transfer cash to a fake bank account.
9 steps to combatting cyber-threats
- A Unified Threat Management (UTM) system
A UTM system is a combination of security appliances and acts as your gateway to the internet. - A SPAM filter
A Spam Filter tops potentially malicious files from entering your network via email. - Antivirus/anti-malware software
Antivirus and Anti-malware are applications that protect your servers, laptops and other devices from malware. - A patch management system
A Patch Management System manages the installation of software updates to close security holes. - 2-Factor authentication
2-Factor Authentication gives you a second level of security, preventing unauthorised sign-ins. - Device encryption
Device Encryption makes any data stored on the machine useless to criminals and keeps your data secret. - A regular data backup
Regular data backups. You should keep a copy of your business data at a secure off-site location in case the original is lost. - Content filtering
Content filtering prevents access to dangerous or illegal websites which reduces the risk of infection. - A disaster recovery plan
A Disaster Recovery Plan sets out how you will recover from an unplanned event such as a fire or cyber-attack.
Regulatory fines and costly lawsuits sting victims of cyber-crime too.
Keeping businesses cyber-secure is even more important since the implementation of the General Data Protection Regulation (GDPR – tailored by the Data Protection Act 2018). Businesses are responsible for their data leaks or breaches if the correct security protections/protocols have not been put in place. Hefty regulatory fines can be levied, and costly lawsuits can follow for the victims of a cyber-attack or security breach.
All businesses should ideally be looking into taking more than just the bare minimum steps to keeping the company cyber-secure, but it’s at least these 9 steps that start the journey in the right direction. The next step beyond the basics is to become Cyber Essential certified.
Cyber Essentials is a Government-backed Accreditation
Cyber Essentials is a government-backed accreditation that acts as a way to understand where your security succeeds and where it needs improvement. It’s similar to a cyber-security audit and allows you to see what your next steps in improving security will be.
Cyber Essentials still covers fairly basic security concepts, such as having the ability to remotely wipe devices, application whitelisting, daily virus scans and the disabling of OS utilities. All of which are simple things that you should already have in place. But it’s well worth going through the accreditation process if you haven’t already – it can improve your company’s image as well as open you up to working with more cyber-conscious clients.
While WhatsApp is a consumer-grade application, many people are using it for business purposes. It’s free and it’s easy to use – most people are probably already using it – so it seems like the ideal communication tool, particularly now many employees are working remotely.
But is WhatsApp really suitable for business communication?
Privacy Policy Updates
WhatsApp was acquired by Facebook in 2014. At the time, CEO Jan Koum stressed how deeply he valued the ‘principle of private communication’. However, just two years later, in 2016, both apps announced they would be ‘coordinating more’– but did give users the option to opt-out of sharing their personal data with Facebook.
This time around, there is no opt-out.
Users who want to continue using WhatsApp after May 15th 2021, have to agree to the updates made to its terms and privacy policy. This means being prepared to share their personal information such as names, profile pictures, status updates, phone numbers, contacts lists, and IP addresses, as well as data about their mobile device, with Facebook and its wider companies. Users who don’t accept the new terms will be blocked from using the app. The new policy, which applies to all users outside of Facebook’s European Region (including the UK), also means that simply deleting the app from the device will not prevent WhatsApp from retaining a users’ private data.
Since the privacy policy changes were announced, WhatsApp has now said that it will not be sharing personal data from people who previously opted out of sharing their information with Facebook. According to The Register, this setting will be apparently be honoured going forward next month, even if you agree to the new policy. For all other users though, there is no opt-out.
A WhatsApp spokesperson also said this update ‘primarily centres around sending messages to businesses to get answers and support’, claiming there will be no change in data-sharing for non-business chats and account information. However, there has been much criticism and concern about the update online.
Update: 12th May 2021
Originally, WhatsApp planned to roll out its privacy policy update on February 8th 2021. However, due to huge public backlash and confusion, they opted to delay until mid-May. Through a series of updates, WhatsApp attempted to clarify its position, reiterating that the update is mainly meant for businesses using its messaging platform. But nonetheless, WhatsApp stated that the change would not impact “how people communicate with friends or family” on the platform. The company also specified in a blog post that it would continue to provide end-to-end encryption for private messages, and it didn’t keep logs of its users’ messaging and calling.
However, despite the clarification around data sharing, there are still plenty of reasons why businesses should stop using WhatsApp for business-related communication
GDPR Compliance and Liability
WhatsApp makes it abundantly clear that the app is designed for personal use in their Terms of Service.
“Legal And Acceptable Use. You must access and use our Services only for legal, authorized, and acceptable purposes. You will not use (or assist others in using) our Services in ways that: … or (f) involve any non-personal use of our Services unless otherwise authorized by us.”
After installing WhatsApp on your device, you’ll receive a pop-up asking for your permission for the app to access your contact. It requests that you ‘Upload your contacts to WhatsApp’s servers to help you quickly get in touch with your friends and help us provide a better experience”. Agreeing to this means that all your phone contacts are accessible in the app. The problem is, it doesn’t distinguish between personal contacts and business ones. Your contacts haven’t given permission for a third party to access their personal data, which could be a potential breach of GDPR.
WhatsApp has been clear that is for personal use. Users must agree to these terms and conditions before they can access the service and WhatsApp can access the users’ contacts. Therefore, the responsibility for GDPR lies with the user, not the app.
Individuals who use WhatsApp for any business communications are in breach of the terms of service. This limits WhatsApp liability for GDPR because they have given the user all the responsibility for seeking the permission of their contacts.
Security Risks of WhatsApp
Using WhatsApp for business communications is fraught with security risks too. While the app famously boasts security due to its end-to-end encryption, there have been plenty of reported hacks and flaws.
Just last October, security researchers revealed that links to thousands of WhatsApp chats were accessible online. Although there was a quiet change to stop the links from being indexed by Google, the information was still readily available on other search engines. The group’s title, image, description and owner’s phone number were all readily accessible, you didn’t even need to actively join the group.
WhatsApp communications are also notoriously difficult for companies to monitor. It may be possible if they are taking place on a corporate-owned device, but even then, there are multiple hoops to jump through. Companies could require the employee to surrender the device, but to access the content itself, there would need to be an IT policy that states WhatsApp as an acceptable communication channel for business purposes. Although, this policy would be in breach of WhatsApp’s acceptable usage policy. The IT policy should be crystal clear about the firm’s right to access and for what purposes (ensuring these are proportionate), so the employee has no expectation of privacy.
Things get even more complex if the employee owns the device and WhatsApp has been installed outside of a mobile device management (MDM) container installed as part of a BYOD policy. The same policy that applies to the corporate-owned device could be extended to employee-owned ones as well. However, given the device is owned by the employee and used predominantly for personal use, it is doubtful whether a forced surrender and access could be seen a legally proportionate.
If there’s no BYOD policy in place? Access is near impossible. As a personal device, the employee would have much higher expectations of privacy and there would need to be an extremely compelling reason, akin to a criminal offence, for an employer to try and obtain access.
What should you use instead of WhatsApp?
While you could write WhatsApp into your IT policies as an acceptable communication channel for business communications, you would knowingly be in breach of the app’s acceptable usage policy.
Plus, even with that in place, there is still a myriad of security, privacy, monitoring and accessibility concerns linked to the app’s business usages. That’s before you even begin to factor in cultural problems potentially caused by the informal nature of the app. Employees could post personal messages to work chats by mistake, accidentally share their live location, or information could get lost between multiple group chats.
Instead, it’s much better to opt for a business-grade secure communication solution. Many of these solutions function in the same way as consumer-grade apps, giving users a familiar interface so they can get started immediately, but with much stronger security. Solutions are available across multiple devices and will protect your voice, video and text data in transit and at rest, preventing accidental leakage or malicious attack.
IT outsourcing is the practice of using an external service provider to deliver some or all of the IT functions required by a business including managing infrastructure, directing strategy and running the service desk.
IT outsourcing providers can take full responsibility for all IT maintenance and support, this is called a fully managed service, or they can provide additional support for an internal IT team, this is sometimes referred to as co-sourced IT support and is usually an approach taken by larger organisations.
A company may use one provider for all their IT requirements, or multiple service providers to deliver different elements.
Types of IT outsourcing
Offshore outsourcing
This involves sending IT-related work to a company in a foreign country, such as India, China or the Philippines, which offers political stability, lower costs and tax savings.
Nearshore outsourcing
The process of sending IT-related work to a company in a country that shares a border with your own. Theoretically, this should make travel and communication between the two companies easier.
Onshore or domestic outsourcing
This involves contracting an external service provider, located in the same country as you, to provide IT-related work, remotely or on-site.
Cloud computing
Contracting an external service provider to provide IT-related services over the internet, such as Infrastructure-as-a-Service, Platform-as-a-Service (PaaS) and Software-as-a-Service (SaaS).
Managed services
This involves contracting an external company to provide network management functions such as IP telephony, messaging and call centres, virtual private networks (VPNs), firewalls and networking monitoring and reporting.
Which IT Services are typically outsourced?
- Application/software development
- Web development/hosting
- Application support or management
- Technical support or help desk
- Database development or management
- Telecommunications
- Infrastructure – hardware, software and network installation and support
- Networking and communications
- Disaster recovery (DRaaS)
- Data centre management
- Data storage
- Security – virus, spam and other online threat protection
There are a number of reasons why businesses choose IT outsourcing. It can enable companies to reduce costs, increase productivity and take advantage of external expertise, experience and assets.
There are a great deal of IT support providers out there, as you may have notice.
So, your company has decided it wants to outsource some, or all, of its IT function to an IT support provider. Finding the right one for your business can be complicated. Putting a business-critical function, such as IT, in the hands of a third party can be quite daunting.
How do you know if your provider is reliable? If your service is a good value? What will happen if something goes wrong?
Interviewing potential suppliers is a vital part of choosing the right IT support provider. Here are a few questions to get you started and the types of answers you should look for.
1. Where are you based?
This doesn’t mean the location of their head office, but more about where your servers are located. This is important if the IT outsourcing company will be providing services such as cloud hosting or VoIP, as it can affect the quality of your services.
GDPR and other laws can also have implications for data storage. Especially for companies working in a highly regulated sector, such as financial services or legal.
2. What geographical areas do you cover?
You no longer need your IT support provider based in the same location as you. However, if you plan to move premises or expand into different countries you need to be sure your provider can support you.
3. As an IT support provider, do you offer different levels of support?
Many IT support companies offer a choice of services levels to suit different budgets and requirements. This may include:
- Pay-as-you-go or ad-hoc support
- Break-fix support
- Managed service support
4. What exact IT Support is provided in your contract?
Be wary of a company that claims to “support everything” without actually going into any detail about what is included. Too often companies think they have complete cover, but discover they can only log a set amount of support tickets a month or there’s an extra charge for certain services. It is better to be clear from the outset on exactly what level of support you would be getting. Otherwise, you risk getting tied into an unsuitable contract. If it turns out what you were considering isn’t quite right you can always ask whether there are different levels of support.
5. What isn’t covered in the IT support contract?
Although you may think this would be covered by asking what is included, asking this additional question will provide you with extra detail. There may be a number of services that are not included in the contract and it is important that you have examples of what may be billed separately.
If there are any services that are not included in the support contract, ask about their ad-hoc or hourly pricing.
6. Do you have any guaranteed response times?
You should expect your IT support company to offer guaranteed response times in the case of a problem. The exact response time may depend on what level of support you are willing to pay for, and there may be different response times for different priority levels. For example for a high priority issue or a P1, the company might guarantee that you will receive the first response in 15 minutes.
It is also important to differentiate between response and resolution times. If your company just says two hours, ask them to clarify if this means they will respond to you within two hours or they will resolve your issue within two hours.
If a company guarantees they will resolve an issue in a certain time period, be cautious. Of course, you should expect a target timeframe, but how can they guarantee when a specific issue will be fixed? It can sometimes take longer than expected to get to the root cause of the problem.
7. Do you provide remote management and monitoring?
Prevention is better than cure. You want a company who offers 24×7 monitoring and is proactive in their approach, taking action to prevent problems which would cause major disruption to your business.
8. Will we get a dedicated account manager if you become our IT Support Provider?
It’s helpful to have a single point of contact at your IT support company, with who you can build a long-term relationship with. They will get to know your business and plans for the future, to ensure IT aligns with your goals. It is reasonable to expect one or two dedicated contacts you can deal with.
9. Will I get a dedicated engineer?
It would be unreasonable to expect to only work with one engineer. All technical staff will have different areas of expertise, therefore it makes sense for an IT support provider to assign the best-suited engineer.
10. Do you work with specific hardware and software companies?
It’s not necessarily a problem if a company works with specific manufacturers, but watch out for those who put their vendor relationship above your business needs. If your provider is vendor-agnostic they will focus on finding the best solution for your requirements, rather than where it comes from.
11. How and when will I be charged?
Terms vary depending on the IT support company. Ad-hoc or pay-as-you-go work typically comes with 15 to 30-day payment terms. Contracted work depends on your company’s terms. This can be billed monthly, quarterly or annually, and is usually payable in advance.
12. How can we raise IT problems with you?
IT problems are frustrating, so you want to make sure it’s easy to contact the company. Ask if your company has a dedicated number, an online support request system or a direct email address. If your contract includes 24x7x365 support, ask how you would contact the service desk out of hours.
13.If I phone you, will I be able to speak directly to a technician who can help?
Does your IT support company operate a call centre where someone simply takes your details and passes it on? Or can you reach the service desk directly? There may be occasions where it’s necessary for your problem to be escalated to a second or third tier of support, but it can be frustrating if you can’t at least speak to someone technical directly in the first place.
This list is by no means exhaustive, but it will provide you with a good foundation when you start interviewing the company that may become your IT support provider.
Digital transformation and automation are hot topics – they’ve been hot topics in one guise or another since IT was born. But despite their proven effectiveness and capability to enhance the way a business operates; many businesses only pay lip service to improving their internal processes in earnest.
Why is this? The two most common reasons are that either they’ve been burned by a project or initiative that was sold to them using automation and digital transformation tags as buzzwords which then failed to deliver substantial results, or they’re distracted by the more visible (but less impactful) new campaigns being generated by marketing or sales.
This obsession with searching for new horizons whilst leaving the internal business to fall into disrepair is seen all too commonly. Even in manufacturing, companies who have been improving their production processes relentlessly for decades seem to have forgotten to apply the same fervour for efficiency gains in the back-office. There are huge gains to be made from automation, but it must be business-led and with a focus on ROI.
So, how do we begin?
1. Understand where you are
This early on, you shouldn’t be looking at the tools to conduct your automation. Nor should you even be looking for external consultants. You need to instead get a general feel for what could be improved and what should be improved in the business.
This is a straight forward exercise of breaking down the business into its component parts – typically into departments. Then list all the business operations/processes within that department, such as client onboarding, lead-processing, invoice processing and debt collection.
You should then break down these processes into steps and actions. If you can use a flow-chart then great, else just map it out in a way that the team understands.
Regardless of what method you use, it is imperative that you are as precise and detailed as possible at this point in your journey. Every concurrent step follows on from this one, so ensure you start on steady footing. The more detail you add, the simpler it is to see areas that can be automated which saves future you time and other resources.
2. Determine priority areas
As you go through your analysis you’ll start to see areas that can be improved quickly. You’ll also typically see that many internal processes can be broken down into two core types of task – actions and approvals.
Taking a typical and traditional expenses procedure as an example: An employee would open an expenses sheet and enter the details of their claims, scan in all their receipts, print the form and receipts, sign the form, hand it to their line manager, they sign-it, it’s scanned back in and finally sent to accounts for payment.
You can see from this that even with simple tasks, there’s a good deal of steps and many opportunities for automation. However, there are also some stages that are impossible to automate – the signatures are a notable example. These can still be digitised, however.
The real purpose of this step is to gauge how and where automation/digitisation can make an impact. By identifying processes that have wide stretches of actions which could be automated or lots of approvals that could be digitised you can create a priority list of tasks that you should address to have the biggest impact. The more steps and touches by people the greater the potential impact.
3. Look at technology
Thanks to the rampant rise of technology and globalisation, you are likely to be able to find tools and applications that fit your requirements relatively easy.
Of course, many systems will be able to take over many parts of your operations and the processes within them. If you can find one system that can deliver greater efficiency and ultimately customer service then it’s potentially going to save you costs, integration headaches and upgrade hassles.
On the flip-side it’s important that during this stage you find a system that maps directly to your requirements, rather than trying to change your operations to fit a system – which can happen with complete business systems that blend various applications and operations, i.e. Practice Management Systems in law firms, ERP in manufacturing, etc.
You may have to create a blend of systems to deliver a highly configurable system. As in essence you then get a much more powerful solution that will deliver you greater results and potentially a greater edge over your competition. Lots of tiny improvements soon mount up into a measurable advantage.
A clear requirements analysis is really going to help you see the gaps when looking at software solutions and systems. Do understand that it’s common to buy a total business system and then not use large pieces of it because those parts don’t truly map to your operations, i.e. you use the accounting and service elements but don’t use the CRM functionality – potentially using a 3rd party solution that integrates better.
4. Plan the project
Once you’ve mapped out your processes, bundled them into relevant categories, evaluated where the big wins will come from and have a solid system/application more or less identified then you have a clear starting point. Now it’s time to look at the project delivery.
A clear time-bound plan along with sensible milestones is essential to deliver returns from a digitisation project. You should be working in conjunction with vendors and (if relevant) developers, along with internal affected teams to create a project plan that you all buy into and approve. It’s important to of course consider costs, not just the hard costs but also the soft-costs – which will often make or break a project in terms of delivering a business-enhancing result.
If you are looking at numerous digital transformation projects, it’s important not to fall into the trap of rolling out too many projects at once or back-to-back. Too many companies go for fork-lift upgrades where they change numerous projects at once and that can cause fatigue and frustration in the user base at best. Create a considered road-map that will give staff time to become accustomed to new ways of working or new systems before undertaking more change.
5. Go hard on testing
Testing can never be overrated. You can only ever deliver an effective digital transformation project through a rigorous and considered testing plan.
Ideally, you’ll be able to pilot the new process or system in a real-time test environment. That way you can see the difference whilst ironing out issues as you go, prior to a wide-scale rollout.
This is increasingly possible now since many applications and systems are now cloud-based, allowing you to trial a system in a fully-fledged test environment without signing up for long-term contracts.
If there isn’t a way to preview the effectiveness of the new process or system, it’s important to agree what success looks like with the vendor far in advance of signing an order or contract. Too many businesses sign-up on a sales person’s promise. A project can fail because clear deliverables aren’t agreed at the start.
If you have stakeholders, i.e. users of the system, ensure that they are happy with the testing. Without stakeholder and user group sign-off you can find yourself surrounded by disgruntlement and finger-pointing. Make sure you tie everyone into success.
6. Go Live
Once you’ve signed off your testing and pilot as a success, it’s time to finish your roll out and go live with your new system. If you’ve got to this stage successfully everyone should be raring to go (communication is everything) and fully trained.
You should now be following your project plan as you bring the solution live. It’s also important to document and analyse any issues that arose along the way. Discuss them in a ‘lessons learnt’ session with the project team during or after the rollout. We all grow through difficulties, and our experiences can help those who follow after us on other projects.
7. Evaluate success
After you’ve delivered your automation project it’s important to formally look back to what your objectives were at the beginning. Did you meet them? It’s also important to do a formal follow-up meeting. Ideally once everything has been running for a few months and then maybe after the first year.
If you can clearly demonstrate the value and business enhancement over a period that’s exciting. It will also transform a boards perception of IT. It will drive it to the centre of the board agenda – which it should be right now.
8. Start again
Digital transformation doesn’t have a clear end. It’s all about continual improvement and so should in effect be a never-ending cycle. It’s very unlikely that the change you have instilled is perfect and can’t be improved.
If you want to grow your competitive advantage and/or profit margin you should be managing change as you go; whilst also revisiting the whole process in specific time-frames. This could be every 3 months, 6 months, annually or longer if appropriate (unlikely).
Ideally, now you’ve gone through the motions, innovation, automation and transformation should have become part of your standard operations. Your board will hopefully be demanding it.
Conclusion
Digital transformation is without a doubt a buzz term. In reality, it’s LEAN and continual improvement rebadged. It’s something every business should be doing in a structured manner to survive and thrive in a global business environment. The challenges are there, but you can gain than ther is to fear.
The story
At 27 minutes past 2 on a Monday afternoon, the phone on my desk rang. Picking it up I was greeted by Faye Langford (a name I was unfamiliar with) asking if she could speak to the company’s CEO, Robert Rutherford. She said she was calling from one of our suppliers (which has been left intentionally unnamed) about an earlier email regarding problems with a credit card.
As Rob was out of the office, I asked if there was anyone else who could help. I was informed that Rob was the only person on the account and so I told Faye that I would pass on the message. She wished me a good day and that was the end of our conversation.
I emailed Rob the details of the call and was content that the issue would be resolved now it was in the appropriate hands.
This all seemed quite ordinary but here are two things which change that:
- There are two people at this supplier who would normally call us regarding card information. Faye Langford is not one of them.
- There are over 15,000 employees who work at this supplier. Faye Langford is not one of them.
So, what had just happened?
The scam
What had happened was an attempt at voice phishing – also known as vishing. When you think of phishing, you probably think of emails but unfortunately, phishing can occur on any channel. Phone calls, SMS or social media are all platforms which scammers can use to fraudulently acquire your details.
But there are some things which make this attempt particularly alarming.
- They already knew Rob’s full name and that he was the company’s CEO
- They knew that we use this supplier and are familiar with the name
- They didn’t probe further when asked if there was anyone else at the company they regularly spoke to
While the information in point one is widely available – on LinkedIn and the company website – it serves as a reminder that scammers will use personal details to make their attacks more targeted and realistic. Had Faye asked to speak to “the CEO”, I would have delved much deeper into what the purpose of the call was. But since she was on first-name terms and was purportedly calling from a known supplier I was more inclined to trust her.
The second point is alarming because it’s narrowly accurate. Since the supplier is well known and works with many companies, this may have simply been a fluke. Alternatively, this may be an emerging worst-case scenario. It’s possible that the supplier has at some point suffered a data-breach and had client information leaked. This would explain how they knew we worked with that supplier and may have been the source of Rob’s details as well.
As it turns out, a few days preceding the call from Faye, the supplier had suffered a data breach. This breach included client’s names, job titles, and partial payment information including cardholder name and card type. This makes it hard to doubt the two events are unrelated.
The third and final point is the most alarming whilst also being seemingly insignificant. When Faye called, she wanted to speak with Rob and was clear that no one else could help when told he was unavailable. This indicates that the scam wasn’t just a scattergun approach but targeted at Rob specifically. Considering that cardholder name was part of the data leaked in the breach mentioned previously, this may be why.
How do vishing scams work?
Based on the articles covering the breach, the information given during the call and other attempts we’ve seen before, the scam would have likely gone like this:
The supplier’s data is breached and acquired by cyber-criminals. This may be sold on a dark-web marketplace to the scammer or the scammer might have been the one to directly take the data.
The scammer creates a fake email pretending to be from the supplier and sends it to the target company stating they need to resubmit card details due to ‘an issue’. This email may include a website link or telephone number to ‘update’ the card details – both of which will be fake.
(I should note that we never actually discovered an email. It’s possible that it was blocked by our email security system due to coming from a known malicious address or linking to a known malicious URL. Alternatively, the email may be entirely fabricated and only used to imply there’s ongoing communication and build trust in the call.)
The scammer now calls the organisation and requests to speak to the target regarding the email about card information. Once they reach the intended target they would likely say that there’s an issue with billing and until the card details are resubmitted, all orders will be frozen and no additional payments can be made.
If the target is worried by this and not suspicious of the request, they will likely be happy to hand over their card details to resolve the issue. The scammer would then check the details are real and maybe say something like “Excellent, I can see the payments are going through now.”, before hanging up.
How can you protect your business from vishing?
Undertake user training
You’ve probably heard this reiterated a hundred times before, but one thing often left unmentioned is that you must ensure your training program is grounded in the scope of the business.
The more abstract training is from employee’s day to day roles, the less engaged they will be and the less they’ll remember. A simulated vishing call against employees whilst in the workplace is not only realistic but will likely leave a lasting impression – making it incredibly valuable.
Don’t rely too heavily on caller ID
Caller ID allows you to put a name to a phone number and identify who’s calling. This sounds like a useful tool in preventing scammers masquerading as someone they’re not. But caller ID can be easily spoofed to show what the scammer wants to show.
There are many online services which offer caller ID spoofing – making it easy for scammers to take advantage of the trust a caller ID can give. This doesn’t mean caller ID is completely useless though as it can be helpful in filtering out nuisance calls, but you should not blindly trust the system.
Don’t respond to requests for details
It’s easy to say this, but if it were easy to do, vishing wouldn’t exist. To keep your details secure, you must get yourself and your employees into the mindset that unless the request is coming from an official channel which the caller can prove is genuine, don’t divulge company details.
Establishing and enforcing acceptable channels of communication for clients can make this much simpler. If you establish in company policy that certain details may never be communicated via certain channels (i.e. never disclose a mobile number over email), it’ll be far easier to stop scammers who are trying to siphon information out of the business.
Take the time to check
If there’s a suspicious call about an urgent bank transfer or new card details, get approval on whether it’s genuine off the phone and ideally face-to-face with who usually deals with the issue (e.g. the finance director). If the caller is genuine, they won’t mind you taking the time to check and if they aren’t, checking is a good way to avoid a disaster.
It’s worth building this approval process into policies so that people know who to go to for each request. Having the process in company policy also shows that asking about the authenticity of a suspicious request isn’t something for employees to be worried about doing.
Employ zero-trust
This policy sounds severe, but zero-trust simply means employees who don’t need to know something, aren’t told it. If you store credit card details in a secure digital wallet which everyone has access to, it only takes one successful vishing call for those details to be compromised.
If only the finance department has access to those details though, it’s much harder for a scammer to get lucky off an unaware employee who was trying to be helpful.
Establish and communicate a list of acceptable requesters
Like with establishing acceptable channels, you should ideally have a list of names for which it is acceptable to give details to. If you’re employing zero-trust, this list only needs to be known amongst those who have access to the details; otherwise, you’ll need to communicate it to the entire company.
… To summarise
Before this experience with vishing, I had only experienced it once before and it had been a rather poor attempt (a very robotic voice asking about the ‘accident’ I had been involved in). I had been fairly certain that this was the way vishing would stay – easy to spot, scattergun and done by text-to-speech. But this latest call has unfortunately proved me wrong.
Not only was it done by an actual real human, but it was pointed at a very specific individual. This is a trend which mirrors the evolution of other cyber-attacks and the increased weight cyber-criminals are placing on social engineering in their toolset. Whilst this threat is old and not uncommon in high-end security breaches, it seems it’s now also coming to the masses.
If you’re uncertain about whether phishing, vishing or any other type of cyber-crime is happening on the scope and scale it’s reported at, I hope this experience opens your eyes to the reality of what’s happening. It certainly did for me.
Lurking deep beneath your surface IT infrastructure is a malignant force. Its creeping tendrils extend into every department of the business and like a rot it spreads.
Whilst it started out innocent, as it grew more prevalent it’s evil nature emerged. Twisting roots buried deeper into the IT environment, corrupting business processes. Tendrils probed out, undermining defences whilst creating unseen vulnerabilities. And a maw guzzled and swallowed all the data it was fed.
But the worst part of all about this malevolent infestation is this. It wasn’t an attacker who planted this thing in your network, no. It was you.
And you continue to let it grow, feeding it and adding to it, all whilst unaware of the peril you have created…
Okay, whilst that description was a little dramatic, shadow IT poses an undeniable risk to your business. Gartner predicted that 1 in 3 security breaches will be the result of shadow IT applications by 2020. And Research from Cisco indicated CIOs underestimate the amount of shadow application running on the network by a factor of 14. That is to say, the CIO thought the business was running 51 cloud services when in reality it was using 730!
These stats highlight how many businesses still don’t have a grasp on the extent of their shadow IT. The risks and controls have been around for years, yet many businesses wait until they get burned to take action.
What is shadow IT?
Shadow IT is hardware or software (often cloud-based) used by staff without knowledge or approval from the IT team.
Shadow IT can present itself in many ways, a few examples being:
- Staff sharing files between themselves, suppliers and customers. Often with a cloud file store such as OneDrive, Dropbox or Google Drive.
- A member of the sales team using an online CRM solution to work on a campaign.
- An account manager using a personal Skype account to conference with clients.
- An employee using an online tool from their previous job, instead of the software their current employer uses.
In each example, it’s obvious that these systems will be outside of the control of the IT department. This is a concern because it increases the business’ attack surface and adds many fun and exciting ways in which your sensitive data could leak.
Shadow IT plays on the idea of “if you can’t see it, you can’t control it”. As a result, it creates a lot of invisible risks and security gaps which the IT team is unable to address.
Of course, shadow IT may be bringing in benefits to a business. If an employee is more comfortable with their tools, they’ll work more effectively. But allowing it to run wild introduces gaping security holes and puts you at higher risk.
Why does shadow IT occur?
Shadow IT arose with the boom in cloud-based technologies and applications. This application explosion allowed employees to gain access to IT solutions through a web interface. And with so much variety, employees could buy an entire suite of tools with little no involvement from the IT department.
The popularity of having sudden access to a plethora of applications was compounded by the fact that in the past, IT projects would have to stop or grind their way through the IT department before becoming usable. Whilst this wasn’t done with malice, the delay it caused frustrated power users who wanted rapid solutions to their issues.
In short, the demand for change was louder and faster than the IT team’s resources, and even their awareness. Technology had come to the masses and they wanted to use that technology. Now.
But blaming everything on the IT department isn’t fair and nor is it accurate. Another fundamental cause of shadow IT is misalignment within the business. Something which involves many departments and generally the board.
A lack of control on the IT estate tends to make identifying a single reason for shadow IT impossible. This means the cause for shadow IT can vary from business to business.
How can I manage shadow IT?
Whilst the idea of prohibiting the use of any applications outside of an acceptable list seems like it would work fantastically, it doesn’t.
Not only will it annoy employees and disrupt their workflows, but people will likely find a way around the filtering or will pester the IT team to add certain applications to the whitelist. Circumventing the point of the system in the first place and only resulting in a net negative.
Instead, the business needs to address the root cause of its shadow IT by installing policy controls and technical controls to reign it in. Here are 7 simple steps to give you an idea of where to start.
1. Review what’s going on
The first step is to use your internal monitoring and control solutions to analyse who is going where and doing what. It’s also worth auditing laptops and desktops if you allow users to install applications on their own devices (not advisable!).
2. Evaluate and prioritise risk
Go through your reports and work out which shadow IT elements pose the greatest risk. Staff sharing sensitive information or accessing the dark web through .tor browsers should both be big red flags.
Whilst doing this, you may also find out you are breaking regulatory obligations without evening knowing it. For instance, by storing files in regions that are unacceptable.
3. Lockdown
Shut down anything that is dangerous or breaking regulation immediately. If it’s illegal or breaks company policy then block it and take appropriate action at a management or HR level.
4. Give an amnesty
Once you’ve dealt with the immediate dangers and know what’s going on give everyone the chance to stop using the unapproved shadow IT applications.
Give them a week or two to alert you why certain applications are necessary and you can then manage the exceptions. After the week is up shut everything unapproved down.
5. Manage relationships
As you work through this process, take care to manage the external perception of the board and IT. People often use shadow IT to better fulfil their roles. So you should be trying to understand why they are using it and how you can fulfil their needs.
You may even find that some shadow applications are of benefit elsewhere in the business and adopting them could be a net positive. You don’t want to turn the business against the IT team as everyone then suffers.
6. Create policies
It’s unlikely that regular employees are aware of the danger of shadow IT and why they shouldn’t use it. Clear policies with training and regular reminders should help minimise risks.
7. Continually manage
You should always be monitoring and evaluating what’s going on in your network. People forget what they’re told, and the odd employee does go rogue. The technologies are out there and are nothing new. So there’s no excuse for not monitoring and blocking employees from doing things that could harm your business.