Every day hundreds of thousands of scam emails flow into the inboxes of users all across the world. While it’s painfully obvious that some are completely fraudulent, phishing emails – particularly those targeted at businesses – are becoming much more sophisticated, and increasing numbers of users are being tricked into sharing valuable company information.
Unfortunately, there is no one red flag which immediately identifies a scam email, but there are a number of things to watch out for.
How to spot a scam email
1. Don’t trust the displayed name in the email
A name displayed in the “from” box in Outlook is not a guarantee of the sender
2. Look but don’t click
If you hover your mouse over a link (without clicking) you will see the web address that the link points. If it doesn’t directly reflect that of the sender then be cautious. Also be extra vigilant if any email directs you to a website asking for a login, as this is the main way a criminal will steal valid login credentials.
3. Check for spelling or grammar mistakes
If the email doesn’t sound right when reading it then that’s a flag that it’s not legitimate
4. Look at the salutation
If your contact usually addresses you by your first name, but now they’re writing “Valued Customer”, you should look deeper. Again, any suspicion you have is probably being triggered correctly – trust your instincts.
5. Never give sensitive information
If an email is asking for sensitive information over email or a web page that you wouldn’t be comfortable with anyone else seeing then pick up the phone to a known number and validate it.
6. Beware of “urgency”
If an email sounds urgent and startling then do take some time to think, analyse or ask advice. If someone is threatening to stop a service or is making a demand then you should stop, think about it, and talk to your colleagues.
7. The images and layout in an email tell the truth
It’s common for cyber-criminals to not quite get the look of emails right, in terms of images and layout. You alarm bells should ring if the email doesn’t look quite right. If in doubt, pick up the phone.
8. Check the domain
Many spoof emails use a domain that is close to the legitimate domain. For example, someone could use paypall.com rather than paypal.com to fool a recipient.
9. Be wary of attachments
Attachments in emails can be dangerous if the file type isn’t a standard application file, such as a .doc (word file), xls. (Excel file) or pdf. (PDF file). Be especially wary if the attachment is one of the following file types – “exe”, “bat”, “com”, “cmd”, “cpl”, “js”, “jse”, “msi”, “msp”, “mst”, “paf”, “wsh”, “wsf”, “vbs”, “vbe”, “psc1”, “scr”, “lnk”. Also be extra careful with zip files as they can often hide dangerous files from inferior email scanners and firewalls.
Example of a scam email
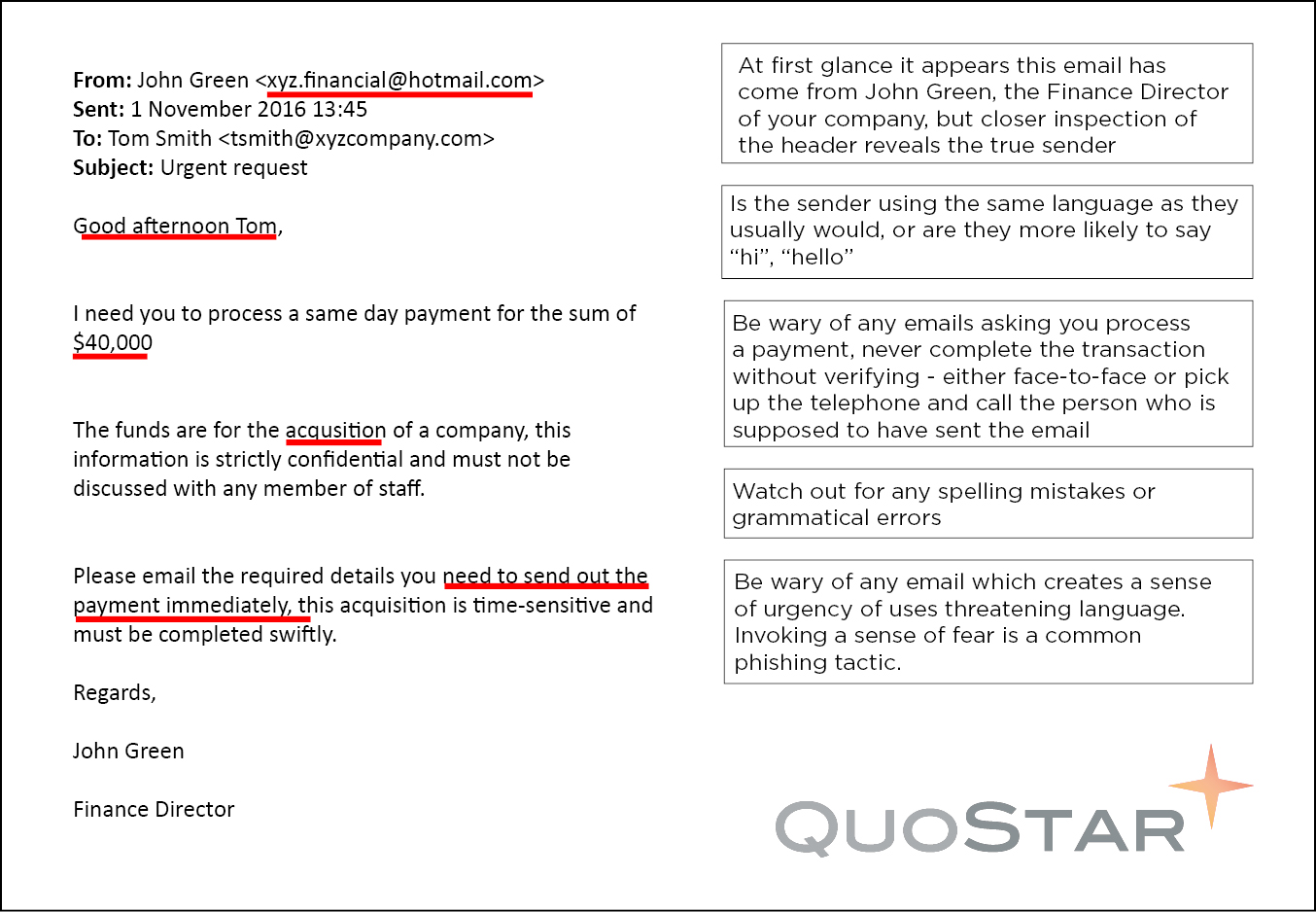
At the end of the day, if an email doesn’t seem quite right then make sure to qualify with the supposed original sender. If your Finance Director asks you to arrange a bank transfer, confirm the request on the phone or in person. It only takes a few minutes and could prevent you from making a costly mistake.
Email archiving brings benefits to every department throughout a business – from finance and legal, through to administration. One department which can benefit from email archiving is HR, as they deal with personal data every day.
Three benefits of email archiving for HR Managers
1. Investigate claims of bullying in the workplace
You may think this doesn’t happen in your workplace, but it’s something you should be able to investigate. Research carried out by the TUC shows that 29% of people have been bullied at work. Email records are important in cases of alleged verbal or physical bullying, as they’re difficult to prove.
An email archiving solution that captures every email provides HR managers with the transparency and visibility required to conduct a fair investigation in the event of a complaint. It’s more reliable than relying on employees to archive their messages on an ad-hoc basis. A solution with user-based security permissions is ideal as HR Managers can investigate complaints without the involvement of the IT department.
2. Monitor for email misuse
A company may find itself in the midst of a legal dispute if employees misuse corporate email. This could range from sharing offensive material to accidentally hitting the “Reply All” button. It is not enough to rely on your employees to use common sense when it comes to email etiquette, and it could result in legal action against your company – as seen in the case of Thales Australia.
One way to ensure employees are aware of your business’s email usage policy is to send a copy of the guidelines via email. Then ask employees to send a reply stating they have read the policy and agree to abide by it. Your email archive will save the reply, so you have a record available should any dispute arise. Using an email archiving solution means you will also have a record of any inappropriate work emails, even if the employees sending and/or receiving them delete the messages from their inbox in between system backups. Emails are time-stamped and digitally fingerprinted at the moment of storage and retrieval so you can guarantee accurate data. Which is essential if these emails are being presented as evidence in a tribunal.
3. Ensure regulatory compliance
You must keep former employees’ records for the duration of employment and for six years after you terminate employment. This includes items like training records, appraisals, contracts, annual leave, sickness records and disciplinary warnings (even if these have since expired). You have to keep these because an Employment Tribunal, County Court or High Court claim is possible for up to six years after employment ends. So the business could be at risk for failing to produce these records. Also keep anything that relates to the employee, which an Employment Tribunal may require as evidence, for this retention period.
Documents are a business asset. If an asset is lost, stolen or damaged, it becomes a risk. Both for the business and for their client.
This means having control systems in place to understand these risks is critical. And having the controls to counter them is equally as important.
It sounds simple. But after a decade of working with businesses, it’s clear that few of them have suitable controls in place. To address this, we’ve created 10 points to guide you through the process of creating your information classification policy.
1. Keeping it simple
When looking at security in any way, it’s important to keep it as simple as possible. This is particularly true when it’s something so regular as dealing with documents.
To make it simple, businesses need to invest in technology. In this case, there are three main technologies worth investing in:
- Document / Content management
- Data leak prevention
- Rights management solutions
A document getting into the wrong hands is going to cause your business, or a client’s business, damage. That is a fact. So aiming to implement all three is the best way to get a comprehensive solution.
2. Mapping your classifications
Before you get into classifying documents it’s important to ignore technology. Technology comes after you have decided the policies and processes you wish to follow.
What this means is that you need to map documents or types of documents into distinct groups. To do this, you should look at two key areas: the sensitivity of the document and their intended audience. This information will make up the foundation of your Information Classification Policy.
Many businesses already have classifications in place. But they’re often created, implemented and forgotten – quickly becoming unusable without weeks or months of additional work. You need to create an Information Classification Policy and not hide it away. It needs to be clear and easy for everyone to work with and conform to with little effort.
3. Building the Information Classification System
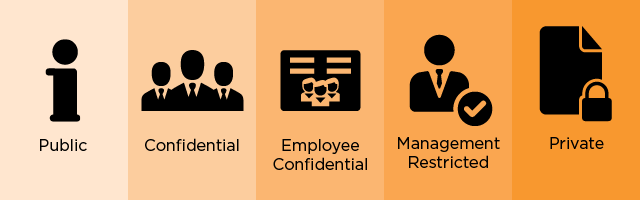
The foundation of any Information Classification Policy is categorising information. Here are a few example document classifications that will fit most business requirements:
- Public: Documents that are not sensitive and there is no issue with release to the general public i.e. on a website
- Confidential: Documents only to be viewed internally or with third parties that have signed a non-disclosure agreement
- Employee Confidential: Documents only to be viewed by employees at the company
- Management Restricted: Documents only to be viewed by the senior management at the company
- Private: Documents which contain personal information (useful for managing GDPR compliance)
In general, you don’t want to go over 10 classifications because classification should be as simple as possible. If you find that you have too many classifications, consider only looking at sensitivity or only looking at intended audience to begin with then filling in any gaps.
4. Assembling the Information Classification Team
A policy needs board-level support to ensure the business buys into and uses it. Once you have this, you should form a team which includes key departments in the business to enforce the policy.
This team may include people from technical, HR, legal and any other departments that are suitable for your industry. An appropriate team will be able to protect a business from security breaches whilst letting people access the information they need. And whilst it is important, the technical solution should be the last point to consider.
5. Designing the Information Classification Policy
Once you have your team assembled, you need to start going through your documents. In most organisations, it can be hard to know where to start.
To solve this, you should group documents at a high level. Looking at the impact that a data breach of that type could cause. Focus on the most sensitive document types first. And once that’s locked down, you can move through the less sensitive list.
When going through this process there are a few tips you can follow.
For company documents, it’s advisable to put your company name first. This helps them stand out from any other classification, i.e. from a client or a partner business.
It’s also useful to colour code classifications to help distinguish documents by eye. This helps you identify a sensitive document that’s left on a screen, printer or vacant desk. The beauty of colour classification is that it aids you in taking action internally or externally. It’s simple to prove that the defendant knew the information was restricted.
It’s important that you make it easy for staff to label and classify documents. If it takes more than three clicks to label a document, staff will find ways to circumvent the system. People naturally take the path of least resistance. So if your system is obtuse, employees will find ways to bypass it.
6. Enforcing control with automation
Once you’ve designed the Information Classification System, it’s finally time to look at the technology. Automation is very helpful to ensure enforcement. You shouldn’t rely on people alone as things will drop through the cracks.
It’s important that any technology links back into the core authentication system within a business. This will typically be Active Directory – the system you use to log in to your PC at the office.
Doing this simplifies things as you can use existing user groups to give access to certain classifications. There’s likely to already be an Active Directory group called “Board Members” for example, which you can use straight away.
Of course, grouping people doesn’t guarantee a user will know who they can and can’t send specific documents to. Nor will it prevent them from sending a document to a recipient by mistake.
This is why a business should be using a Rights Management system. Rights Management ensures that the systems know who has permission to access the document. So even if someone does send a restricted document, the recipient won’t be able to view it.
7. Educating employees
One of the largest reasons for data leakage is employees. Make sure to train them on how to use systems and refresh them periodically.
Also educate them on any security risks to the business – known, current or potential. They need to understand why following policies is important and how not following them can impact the business and therefore them.
8. Controlling leavers
So many organisations do not manage ex-employees. It’s important to disable their accounts once they leave the company. Even if they left on good terms, it’s best not to take a risk.
Loose accounts complicate the system at best and act as a open hole for attackers at worst. Hackers or insiders can hijack old accounts and make use of the access privileges. So you need to shut down accounts or strip them of all access rights to reduce the risk to your data.
9. Continually improving
It’s best if you adhere to common processes and document them somewhere accessible. To do this, you need robust information classification and risk policies that integrate with a wider standard. A good example to use as a framework is the ISO 27001 standard.
Doing this ensures that you assess and improve how you are controlling your risks within the business. Keeping you protected from an evolving threat landscape.
10. Widening the focus
It would be ridiculous to only focus on document security whilst ignoring the other risks to your business. So understanding all the risks your business faces and assigning suitable controls is something you must do.
Again, the ISO 27001 standard is a good framework to use for managing your information security on a wider basis. But this shouldn’t stop you going ahead and dealing with document security first. Getting this done will make things easier in the long term.
Summary
Businesses must control their risks, as failing to do so has catastrophic consequences. The key is to start simple and then improve. You don’t have to adopt everything at once.
A good starting point is to understand the sort of data you have and then classifying it. A good percentage of your business information could be used to extort or embarrass you. Or even worse, a client.
Once you’ve got your classifications, tie them into document templates. Then automate management and workflow automatically with technology. When done right, businesses can dramatically improve their security since it’s embedded onto the asset. Rights Management can then control who can edit, copy, paste, print, email, transfer or view it at a later date.
Once in place, this can be overlaid with network controls such as Data Leak Prevention. This watches documents flow in and out of the business and can isolate, sandbox or alert relevant people that a breach may occur.
To take it further, systems at the perimeter, such as gateway encryption solutions, can identify sensitive information. Encrypting it to ensure it won’t pass over the open Internet in clear text.
The list can go on but it’s important you start at the beginning by creating an Information Classification System. You need to understand what you have and what the risks and potential controls are first though.
There are typically three ways in which businesses can archive their email; save absolutely everything, rely on users to archive emails or utilise an email archiving solution.
With 269,000,000,000 (yes, that’s billion!) emails being sent and received every day, storing every single one is not really feasible. And with 200 billion of those being SPAM, storing each one is unnecessary, only serving to increase the cost and length of the e-discovery processes.
Neither is it reliable to depend on users to archive their own emails. If they forget or were unaware what they needed to archive, your business has to pay the price if the email is needed for litigation or audit purposes. An email archiving solution, on the other hand, automatically archives, stores and preserves emails for you.
How can your business benefit from email archiving?
1. Reduced storage requirements
Archiving solutions typically use two different techniques to reduce the amount of storage required, neither of which will affect end-users. Advanced compression technologies compress each email and its attachments before archiving, saving 50% or more in overall storage requirements. De-duplication, also known as single instance storage, ensures that the archiving solution only stores one copy of each message or attachment.
2. Prevents users from losing data
Users can easily delete important emails, accidentally or maliciously, and the majority often delete emails between backups, and at times the entire inbox upon leaving the company, which means your business is at risk of losing important data. An email archiving solution can eliminate these risks, by automatically storing and preserving all emails.

3. Increased server performance
Moving emails out of a live environment will help to greatly improve the performance of your email server. Emails can be deleted from the mail server, according to rules-based processes, once they have been archived and stored.
4. Simplified backup and restore
Reducing the email server’s data load allows it to be backed up faster and more simply. Users can also restore emails from the archive to their inbox with a single click, freeing up your IT engineers from having to go through the time-consuming process of recovering them from a backup.
5. Eliminates mailbox quotas
An email archiving solution removes the need to use mailbox quotas as a way to limit the use of a mail server’s storage capacity.
6. Accelerates search capabilities
Most archiving solutions will provide a basic search and retrieval function for data that has been stored and retained. Some solutions will go further and allow users to search by email address, to/from address, attachment name, words within documents, plus more, drastically cutting down the time it takes to locate an email.
7. Accounts for all users
With an archiving solution, you don’t have to rely on users adhering to email retention guidelines. All emails will be automatically stored, archived and preserved.
8. Eliminates PST files
Individual PST files are prone to data corruption or loss, have a huge impact on storage and can be difficult to search through, due to their size and number. With an email archiving solution you can import all historical PST files into the solution, which you can then search with ease.
9. Helps ensure compliance
Many sectors have specific rules and regulations regarding data retention, and an email archiving solutions help ensure you remain compliant. All business must be able to pull back emails on demand for the purpose of litigation or auditing.
10. Lowers costs
Email archiving solutions will typically work effectively on cheap storage, whereas most email server systems require faster, more expensive disks and technologies. The majority of companies will see their data usage grow every year, which will equate to increased storage costs and increased storage management costs.
11. Removes human error
User-driven retention relies on users managing retention with predetermined tags and rules, for specified time periods. This method of retention is prone to user error because you rely on users to consistently adhere to and follow the guidelines. Even with constant policing, it would be easy for a user to “forget” the guidelines, or intentionally ignore them.
12. Typically tamper-proof
While users can search and retrieve emails from the archive, most solutions are tamper-proof – an essential feature for compliance. Not even the IT department will be able to alter or remove emails from the archive. The solution should also have a tamper-proof log which records who reads what in the archive and when they read it. All emails should also be digitally signed to allow them to be used as evidence in a court of law.
There are many types and forms of email archiving solutions available. Some will go beyond the benefits listed here but others may not be as effective. It’s important to carefully research available solutions, both internal or cloud-based, so you can find the right one.
An email archiving solution is critical for your business, and not just so you can comply with regulations. A huge amount of business-critical information is on the IT systems. Some of it may exist solely in email so it’s vital that you don’t lose this.
A large percentage of business decisions are now made completely via email, yet many organisations have no retention policy in place to protect those messages.
While those businesses may have been lucky up until now, there will likely come a time when they need to retrieve a historical email. At best, they will have to spend time searching for that critical email, but they could end being penalised financially.
However, it can be difficult to establish just how long you should be keeping your emails for. Does every email need to be kept indefinitely, or do different rules apply to each email?
Outlined below, is a brief description of the primary regulatory bodies or regulations which apply to email retention. All organisations should have a clear understanding of the ones which affect them so they can develop an effective strategy.
What are the regulatory bodies?
1. Employment Tribunals
Employers should assess different retention periods for different types of employment data as the Data Protection Act only states that “personal data should be kept for longer than necessary”. Job applications and CVs only need to be kept for a short period of time (e.g. six months). If you wish to keep a CV for future reference you must inform the applicant you are doing so. Personnel records of former employees should be kept for a maximum of six years. Employment tribunals, county court or high court claims are possible for up to 6 years after employment is terminated, so keeping records is considered acceptable on the basis that the employer is doing so to protect against legal risk. For specific documents, like PAYE records or maternity pay, the employer must assess the appropriate guidelines and determine a retention policy.
2. Court Action under the Civil Procedure Rules
Businesses could be at risk if they fail to produce evidence, which may be contained within an email, for auditing or litigation purposes. It is possible to bring a claim for a breach of contract up to six years later, so businesses need to be able to respond quickly. Furthermore, the amendment to the Civil Procedure Rules and the issuance of Practice Direction 31B, Disclosure of Electronic Document essentially mandates that businesses must be prepared for electronic discovery.
3. The Data Protection Act (DPA) 1998
Requires companies to ensure they have taken the appropriate technical steps to protect any personal data they hold from misuse, theft or damage. If a DPA request is received then an organisation has 40 days to provide a copy of this information.
4. Freedom of Information Act
Provides public access to any recorded information including emails and computer documents, held by public authorities. This includes government documents, local authorities, state schools, universities and the NHS.
5. Financial Services Act
The financial services industry is strictly regulated and requires financial organisations to store all business emails sent and received for up to 6 years. Some data must be kept indefinitely so that cases can be reviewed.
6. The Sarbanes-Oxley Act
The US passed this Act, which introduced stricter financial reporting requirements, following two financial scandals. The aim was to protect shareholders and the general public from accounting errors and fraudulent practices in the enterprise. It can also apply to UK companies if they are subsidiaries of certain US companies, and the Act places requirements to retain business critical emails. Rather than specifying how a business should store records, it defines which records should be stored and for how long.
What do you do now?
As you can see from above, there are many regulations to consider – and this is just a brief overview! There are many other specific retention periods. For example, medical examination records and registers of employees working with hazardous substances must be kept for a minimum of 40 years, under the Control of Substances Hazardous to Health Regulations 1995/3163.
All emails need to be treated differently. When deciding on your policy it is recommended that you:
- Consider legal obligations and business needs
- Establish standard retention periods for different types of information
- Ensure information is kept securely and also destroyed securely when no longer needed.
There are three typical retention policies used by most organisations. Option 1 is to Save Everything, which means all data is retained for use in any litigation matters. While this may seem the safest it will cause issues. There can be decreased performance, prolonged backup and restore processes and extended e-discovery costs – as more data stored equals more data to search through.
Option 2 is User Driven Retention, where users manage retention with predetermined tags or rules. Theoretically, this should mean that the organisation only retains what it needs to, but it depends on the users. There is a high risk of human error as users must remember and understand all retention guidelines.
The third option is to automatically archive emails, which can be carried out by an email archiving solution. It is not feasible to keep every email in a live environment. As volume increases, simple operations like search and retrieval become more time-consuming. An email archiving solution fixes retention periods for emails, which are controlled by automated processes. It provides secure storage for all users to enforce compliance and is ideal for many businesses – particularly heavily regulated industries.
Ransomware is a type of malware designed to block access to a user’s system or files until a ransom (usually paid in a cryptocurrency such as bitcoin) is given to the hacker.
There’s a multitude of strains of ransomware out there. Notable examples include CryptoLocker, Crowti (also known as CryptoWall), Tescrypt or Teslacrypt, Teerac, Critrioni, Reveton, Troldesh and WannaCry. But all of these can be simplified down to two main types: encryption ransomware and splash-screen ransomware.
What is encryption ransomware?
This is the type of ransomware most people are aware of. It works by encrypting any files it can discover. Which can be anything from important documents to corporate databases, to personal photos and videos. Once encrypted, these files will be rendered useless. And in most cases will have their extension changed to make them unopenable.
Encryption ransomware will typically use a type of encryption called asymmetric encryption to lock your files. What this means is that the encryption key that encrypts your files is different to the decryption key which decrypts your files. Making the only way to get the decryption key and access back to your files – if you have no backups – is paying the ransom.
What is splash-screen ransomware?
Splash-screen (sometimes called lock-screen) ransomware restricts access to your files by placing an unclosable, unmovable and persistent window on your screen. The only way to remove this screen is to pay the ransom and only then will you be able to access your files and programs again.
Sometimes these splash-screens just include a message telling you that you’ve been infected and need to pay a ransom. But sometimes hackers take things a step further, including the logo of the police, FBI or similar organisation, then claiming that your computer has been locked due to illegal or malicious activity and demanding you to pay a ‘fine’ to have it unlocked. This, of course, is just another example of hackers using social engineering to try and coerce victims into paying up though.
How can you protect yourself against ransomware?
If you’re simply relying on anti-virus to protect you from ransomware, then that’s not a great business strategy. A new malware specimen emerges every 4.2 seconds and while anti-virus protection can block some of these. Other variants could slip past the filters. Luckily there are lots of other tactics you can implement:
Invest in employee training
Employees are often the weak link when it comes to security. You must make them aware of the impact their day to day actions can have on the business. If your workforce is unable to spot a phishing scam, for example, then your company is vulnerable. Investing in security awareness training can be greatly beneficial for your business and will help employees.
Perform regular back-ups
You should already be doing backups as part of your business continuity. But if you’re not, then make it a priority to perform regular, point-of-time back-ups you can restore from. Continuous back-up is ideal, but at the very least, you need to be doing one backup every day.
Even then though, a ransomware attack would mean losing a day’s worth of work. Something which could be a significant loss to a small company, let alone a large one. So make backups as often as possible.
Ensure backup locations are not networked
It’s no good to backup all your data if a ransomware infection can locate and encrypt it. Making sure that the backup location is not a mapped drive is one way to do this. Don’t copy files to another position on the PC, instead backup to an external drive which does not have a drive letter or which you only connect when performing the back-up.
Regularly patch or update your software
Hackers often rely on people running outdated software with known vulnerabilities which they can exploit. To decrease the likelihood of ransomware infection, make a practice of regularly updating your software. Alternatively, look into patch management for your business as a way to automatically manage the installation of patches for you.
Layer your security
Whilst relying solely on anti-virus is a bad idea, that doesn’t mean you should get rid of it altogether. Anti-virus should be one layer of your overall security suite, containing anti-malware software and a software firewall. A system like UTM can help you with this.
At a minimum though, ensure you are scanning at the email gateways, firewall and end-user devices if you are relying on anti-virus.
Filter .exe files in email
If your gateway email scanner has has the ability to do so, you may wish to set up a rule to deny emails sent with the “.exe” extension. .exe files, or executable files, are capable of executing code which can be used to instigate a ransomware attack. There are other types of extension capable of executing code to be aware of. But .exe is the most common one.
Conclusion
Ransomware is a dangerous threat to both home and business users of technology and as a result, needs to be treated that way. The worst thing you can possibly do is think that it won’t affect you. Anyone with an Internet connection is a potential victim. And hackers don’t care if they’re targeting individuals, small businesses or multinational enterprises. All they care about is taking your money.
Remote access to internal IT systems is still a big enabler for any sized business. Business is no longer 9-5, and staff are no longer just sat in the office. The world has changed, so surely remote access has as well? Well, not as much as you’d think, but bandwidth has dramatically improved, as has its cost and ease of access. You can get a decent internet connection virtually anywhere in the world; this has made remote working productive and cost-effective.
What remote access technologies currently exist?
In reality, the technologies haven’t really changed much over the last 10 years. There’s a lot of hype surrounding numerous technologies, but at their root, they aren’t particularly new.
I’d say that we are generally seeing the decline of traditional client-VPN technologies (SSL and IPsec) to access files and folders, where you have an application loaded onto a PC/laptop/tablet and you connect to a corporate network. They are typically cumbersome and problematic to support. I would ass that this has changed a little with the rise of WAN accelerators and solutions such as Microsoft One Drive, but it still can be a little cumbersome to manage.
You will find that a large percentage of corporate applications have web-based front-ends these days. These are often more or less indistinguishable from applications installed on the desktop, feature-rich and simple to support. They typically lend themselves well to being published over the internet for roaming workers to access the internet. A typical example of this would be Microsoft’s Outlook Web Access.
A favourite technology for remote access and general working is thin client. There isn’t really much difference in the method of access to internal IT system cloud-based based ones.
Is it all about the cloud?
The cloud is generally remote computing, and thus remote working. However, corporations have been working to this model for decades, satellite offices accessing systems in remote headquarters on the other side of the world. Now because somebody put a shiny new cover on in, everything thinks cloud technology is all new. It’s not new, neither is cloud always the answer. If you have systems internally that you want to access remotely, it’s usually quite a straightforward exercise. That’s not to say that the cloud isn’t the answer to many business requirements, it’s just unlikely to be justified on remote working alone.
The risks of BYOD
We hear about BYOD (Bring Your Own Device) daily – accessing corporate systems with a user owned device. However, generally it will typically incur greater IT management, integration, administration and IT security costs – well it should do if implemented correctly (at this point in time) to remove any security risks: you aren’t going to accept significant risk within your business. If a business doesn’t own a device they can’t really control it. Then you can’t stop third parties from accessing the device, or from dangerous software being installed on it and circumventing corporate security, it’s as simple as that. Yes you can get encapsulation technologies that act like a secure operating environment on a device, but I’m still cautious. I’d still use these technologies, but with a corporate owned device.
I’m a bit more of a fan of CYOD or Choose Your Own Device. This is where an employee can select a device from a pre-authorised list, easing support overhead and ensuring productivity. Have you ever actually really tried to use an iPad productively? It just doesn’t compete with, say a laptop. However they are fine as additional devices for intermittent emailing and reading on the fly, etc. I also find that CYOD does help staff morale – it’s nice to have a choice, and computing devices bring up similar emotions to getting given a company car.
Also, I should note that it was only a few years ago that everyone was talking about increasing productivity within the workplace through IT. Can you really do that when everyone’s walking around with their own mobile devices hooked up to the internet with a 3G card? I understand there are always exceptions, but generally the money saving case will not stack up under scrutiny.
Generally, you haven’t moved away from Windows Server 2003 because a critical and extremely complex piece of internal software relies on it, or due to budget constraints. There are a few other reasons, but chances are that you are simply being negligent and putting your business at risk for the sake of saving a few £s. If you are ignoring the end-of-support warning due to financial concerns, then you are playing a dangerous game. In fact, if you are unfortunate, a savage enough attack could cripple your business or even put it under – and that’s not scare-mongering.
You will notice a few security vendors stating that they can protect you whilst you still run Windows Server 2003, but generally, this isn’t really the case as the weak link often comes in a process or a person. Also, if they were all so good we wouldn’t have any viruses or exploits, would we?
So, if you are in a difficult situation, where do the real threats lie?
- The server faces the Internet directly, i.e. many hosting companies give a customer a server with a live Internet address (IP) on it. The customer then installs a software firewall on top of the Windows 2003 operating system.
- The server indirectly faces the Internet, i.e. it’s connected through some sort of physical/virtual firewall, i.e. the server is acting as a web server, client portal, FTP server, etc. Even if the firewall has advanced intrusion prevention the risk is significant.
- The server is not accessed from the outside world but initiates communications,e.g. it is a Terminal Server/Citrix server, proxy server, etc. The threat comes from the server hitting a website with malicious code and fires an exploit that compromises that server and the LAN/WAN it sits on.
- The server sits on an open LAN with other network devices, such as PCs, laptops and other servers. Although these other machines may not be able to be infected – they can still potentially pass on ‘an infection’ to an unprotected Windows 2003 server.
- The server has other devices plugged into it at times, i.e. USB storage devices. The risks are lower here but still real.
There are other risks but these are the main ones and the most significant. Over the coming months, the risks to Windows Server 2003 are going to be pretty large as hackers and the like hold back exploits until the support ends. The flames will burn brightly for say 6-9 months and then slowly taper off as the easy prey has been picked off and the bandits look for new pickings.
If you have left it too late to switch from Windows Server 2003 then what are the key things you can do to protect your environment?
- Don’t connect it to the Internet directly or indirectly.
- Segregate it via the normal LAN via a VLAN and/or a firewall device.
- Any connections to it from internal pass through an intrusion protection firewall.
- Don’t plug any external devices into it.
- Plan to migrate services from Windows Server 2003.
The important thing to do is plan to protect services as soon as possible, then get your plan ready. Depending on the size of your environment, it’s unlikely to be a straightforward task, so you should probably start planning now or bring in a consultant quickly. You need to take a number of factors into account as a bare minimum. Here a few generic ones to get you thinking about the implications.
The implications
- Will your existing hardware support new operating systems and/or software?
- Do your IT staff need training to roll-out and manage the new operating systems and/or software?
- How will you overcome any compatibility issues?
- Will your other applications work on the new operating systems and/or software?
- Will your 3rd party application vendors support their applications on a new platform?
- How long will it take to test everything?
- Will you need to train other employees to use the new operating systems and/or software?
- What resource will you need to roll out the new operating systems and/or software?
- How long will it take to roll the new software out?
- What are your other options? Could you go thin-client? Could you go to the cloud?
- What do you need to budget for?
If you’ve been avoiding a move due to expense then remember that everything can be turned into an OpEx. This does help financing and budgeting immensely. You can go for a fully managed cloud, your own private cloud, or simply replace servers and software in-house. You can also finance development work and consultancy and wrap it into a monthly payment.
Running Windows Server 2003 past the end of support will likely leave you open to regulatory issues. It will also leave you open to a lot of issues from an insurance perspective should a breach happen. Also, how about the embarrassment of your breach in the press? I know I’ve been quite strong in my views here on a bit here, but this has been on the radar for years, there is no excuse.
Not taking action now is simply like knowing the spare bedroom window won’t close properly. Chances are at some point someone’s coming through it.
Any device where data is downloaded or stored is at risk of being accessed by a third party once it is no longer in your possession. Devices at risk range from the obvious hard disks, right through to printers.
The basic principle is: if data is written it can be retrieved unless it’s encrypted. Therefore, if you’re in an industry where your clients’ data is sensitive (which is to say, every industry), if you can encrypt the data you should always do it. Of course, you need to factor in performance overheads in relation to encryption but that is becoming less of an issue now with the entry of technologies such as solid-state disks and self-encrypting storage arrays. Encrypting data effectively removes a lot of the concerns around the disposal and/or loss of a device.
If you do have to dispose of a device then it is usually best to have it done by a third party specialist data destruction firm. However, you need to be aware that by choosing to outsource this function, you are not outsourcing all responsibility. If a client’s data were to be stolen from one of your disposed machines, it’s your brand that will be tarnished, therefore you have to do your due diligence. Assess the data destruction firm and assess your risks. Do not simply settle for a van turning up to remove the worry.
Once you identify the risks you should have them signed off at partner level and agree on a strategy to apply suitable control to minimise them. If you can follow these steps you can be pretty sure that your clients’ data and your firm’s reputation will remain safe.
Don’t think that PCs are the only source of data that can unintentionally (or maliciously) disclosed to a third party though. You should also have security and disposal policies covering the following:
- PCs, laptops, tablets
- Mobile phones
- Printers
- USB storage devices
- CDs/DVDs
- Servers
- Hard disks
- Backup tapes
- Cloud storage
Again, all of these items can be encrypted and, arguably, they all should be if your data could cause your firm or a client embarrassment.
Risk of extortion
Never think that your information is not of interest to a third party. A large proportion of data and security breaches are now focused on blackmail and extortion. Hackers hack for money now, not simply for fun. A hacker doesn’t have to come in over the wire, getting hold of a physical device littered with information will give them extortion material and valuable clues on how to breach network defences at a later date.
Your key considerations
So, what are the key things to consider in relation to ensuring data is destroyed after its useful life? In this article, ‘destruction’ refers to physical destruction (shredding) and ‘wiping’ to cleaning the data off securely, to retain some resale value to the firm or a third party.
1. Control access
As you can imagine, it’s possible that, if you leave a pile of hard disks or USB keys in an uncontrolled area, once could go missing. And if this happened it would be open to all risks. When you have set aside equipment for disposal then secure it away from general access.
2. Control / document assets
Make sure your asset lists are up to date so when you wish to ensure any data is destroyed you don’t miss anything. If you aren’t controlling your assets then you aren’t truly controlling the risks. When you do dispose of an asset, ensure the information is logged, including the device, serial code, how it was sanitised, by whom, when, where it went, etc. If you go to a third party it should provide you with a certification of destruction.
3. Destroy the data
If you just format or delete the data on a device it’s relatively simple to pull it back. If you want to ensure the data is irretrievable then you can use specialist tools to do so. You can start by looking at tools such as Kroll Ontrack and Blancco if you want to do it yourself. If you want to go belts and braces, encrypt the device storing the data and then run the secure erase tools. You then, of course, need to factor in the time required to undertake this work. It all comes down to how sensitive your data is.
4. Destroy the device
In some circumstances, the data is so sensitive that the entire device should be destroyed, shredded in fact. Generally, you would outsource this, but you can also buy the specialist equipment to do it yourself. Typically memory and hard disks are shredded, and other parts of the device sold on to retrieve precious metals. There are strict environmental guidelines on disposal of equipment so be sure to familiarise yourself with the current regulatory requirements if you do it yourself.
5. Destroy it quickly
Once you have identified equipment to be disposed of or wiped, then do it quickly. The longer devices hang around, the more chance they will fall out of control or go missing. You would typically expect to have a periodic destruction cycle or pick-up if using a third party.
6. Have a process
Ensure you have a documented process for the destruction of data and devices as required. If you don’t have a rigid structure, things can and will slip through. Generally, legal firms can’t risk that happening so controls and processes must be put in place and followed. Failure to follow procedures must have tough disciplinary repercussions.
7. Check third parties
If you are outsourcing the destruction of data and devices to a third party then ensure that you are careful in your choice. There have been press reports of devices turning up on sites like eBay with very sensitive data on, even on a printer’s internal flash disks. So, when choosing a service provider, you should be looking for companies with ISO 27001 and ISO 14001 certification as a bare minimum. Also, it helps if they are certified to destroy MOD equipment, e.g. CESG and MOD approved. The higher-end secure destructions firms will also have the equipment they can bring to your premises or premises you can visit to witness the destruction of your data devices.
8. Communicate and review
Once you have a process and policies in place to relation to wiping and destruction of data and devices then ensure that it’s communicated and clearly understood. Make sure all relevant areas of the company understand their roles. Also once created don’t just forget about the policies and processes, review them at least annually. Your assets will change, as will the risks. Ensure that you review them regularly and know what they are
Security is changing
As we look back over this tiny area of IT security, the case for ISO 27001 is becoming more and more important in law firms. The risk of a security breach of any kind can have serious implications more so now than ever before. ISO 27001 will give a firm a framework to identify all risks and assign appropriate controls to mitigate them. It will also give your firm a continual improvement methodology that will deliver gains year on year. It should also be noted that many clients are now demanding ISO 27001 certification as a standard before instruction.
As a final note, just do remember that your data is of interest to many people. Don’t take risks, or at least don’t take them without informed sign-off from your firm’s partners.
Security as a service (SECaaS) is the outsourced management of business security to a third-party contractor. While a cyber-security subscription may seem odd, it’s not much different from paying for your anti-virus license. The difference is that SECaaS is the combination of a lot of security products wrapped up into one more central service.
The range of security services provided is vast and goes down to a granular level. Examples range from simple SPAM filtering for email, all the way through to cloud-hosted anti-virus, remote automated vulnerability scanning, managed backups, cloud-based DR and business continuity systems and cloud-based MFA systems.
The services are either delivered directly from the vendor where the reseller takes a commission or they are delivered from specialist firms who have the in-house skills capable of building, integrating and managing specialist security services for their customers.
Just a note here: you may have heard of SaaS (software as a service). This is different to SECaaS.
1. Is SECaaS dangerous?
Putting your security in the hands of another business may seem like a big risk. And if done incorrectly, it’s almost guaranteed to have a less than ideal outcome. But businesses have had success with SECaaS and there’s no reason you can’t either.
The most likely cause for an issue is choosing a supplier based solely on price. A business offering SECaaS that’s been around for a few years and has a range of clients but charges £50 per user per month is going to be very different from the business that offers “cloud-based security” for £10.99 per user per month.
Do not instantly go for the cheapest option when considering SECaaS.
Sure, you might be paying nearly 5 times as much. But if your SECaaS provider has the lowest price on the market they’re skimping on something. And if there’s one thing you don’t want to skimp on, it’s your cyber-security.
2. What are the advantages of SECaaS?
Cost-saving
Despite what was just said about avoiding cost-cutting when it comes to cyber-security, one of the main draws of SECaaS is the long term price savings it can have. Because you don’t actually own the infrastructure, you don’t need to pay for its floorspace or for its upkeep (prices which can fluctuate based on external factors). Instead, you only pay a flat rate that is unlikely to change.
Fully managed
Your provider is the person keeping up to date with the changing threat environment, not you. That means that you can focus more on your own business goals instead of diverting time towards understanding the various threats out there and ensuring that your defences deal with them.
Greater expertise
A good SECaaS provider is going to consist of people who know everything there is to know about cyber-security and regularly keep up with trends and changes in that area. As a result, they’ll have a much greater range of expertise which you can utilise to keep your business safe. This also lets you keep your core employee focus on your own sector rather than branching out and getting a dedicated cyber-security expert.
Frees up time from repetitive tasks
Time-consuming admin tasks that need to be done can be performed by your SECaaS provider instead. This can be things like reading system logs or monitoring the overall network status.
3. What are the disadvantages of SECaaS?
Reliant on SECaaS provider acting
This is the main reason that you should be choosing a high-end SECaaS provider.
Because SECaaS providers are the holders of a lot of data, they (and as an extension, you) become lucrative targets for cyber-criminals. If they are breached then you are breached so ensuring they have made big investments into their security is paramount.
To make sure that your chosen provider is continually investing in their security, be sure to keep in regular contact with them. Ask questions about what they are doing to address the latest types of exploit or flaw and dig deep into the specifics of what type of security they have in place on their own systems. Is it minimal or is it high-grade and comprehensive?
Whilst in the decision stage you should also be asking each provider exactly what kind of security they have in place or what is their policy is around topics like staff training. If they can’t prove that they are taking their own security seriously, you can bet that they won’t be taking yours seriously either.
Increases vulnerability to large scale attacks
The uniform security measures SECaaS providers have over multiple clients allow them to keep up a comprehensive level of security. But it also means that if a vulnerability is found for a business who use the same SECaaS provider as you, then that same vulnerability can be used against your security.
Because one vulnerability gives so many potential attacks for a hacker, probing the security of the SECaaS provider is much more rewarding for cyber-criminals. This means they put in a more concerted effort towards breaching the SECaaS provider’s security. This can inadvertently make you a prime target for cyber-attacks.
Be aware though, as a business (even a 2-10 employee one) you’re already a prime target for cyber-attacks. If done properly, the perceived increased danger of choosing SECaaS can be made negligible. Especially when compared to the increased overall security you would receive from a high-quality SECaaS provider.
3. Why is SECaaS being offered more often?
Security providers are becoming aware that with the rise of small businesses. There’s a growing market for security services that don’t need expensive internal employees or risky infrastructure investments.
Many growing businesses also don’t have the up-front funds to develop a hardware heavy security system. Therefore, they find a monthly plan to be much more manageable for their finances. For example, implementation of two-factor authentication and disaster recovery may have cost £100K five years ago. But SECaaS can deliver the same project on a £1,000 budget with no CapEx.
Because of the flexible nature of SECaaS, many of the decisions can now be addressed head-on. There is no longer the same level of risk anymore surrounding topics like setting up security infrastructure. Businesses can switch SECaaS providers more easily. So, this ‘de-risking’ of cyber-security has made the SECaaS market ideal for businesses who want to avoid making a bad decision.
Finally, with the rise of the cloud and increased internet speeds. Services offered over the internet are now on a par with in-house solutions. This has meant that cyber-security being offered as a service is now very feasible and is genuinely useful.
Conclusion
So, you may now be asking yourself if you should consider SECaaS for your business. Unfortunately, there’s no comprehensive answer. If you want to improve your security, without draining your budget, then it’s worth reviewing. But if you already have a fairly comprehensive security setup in place it may be better to ensure that it actually is as comprehensive as you think it to be and then just sticking with what you have, upgrading it and maintaining it as you already are. Alternatively, you could look into a UTM system for your business if you’re uncomfortable with SECaaS but want to make your security more comprehensive.