



What is warshipping?
What is warshipping?
Warshipping is a type of cyber-attack in which criminals use physical package shipping services to send malicious hardware to a victim or hide malicious hardware on the business premises. This hardware can be remotely controlled by the attackers and used as a staging post for further attacks.
How does the warshipping cyber-attack work?
Warshipping uses custom-built devices consisting of cheap, easily available components: a single board computer (£30), phone battery (£15) and IoT modem with 3G connectivity (£35). The resulting device, or ‘battle package’, can be smaller than the palm of your hand and, once configured, is easily concealed and shipped to a target.
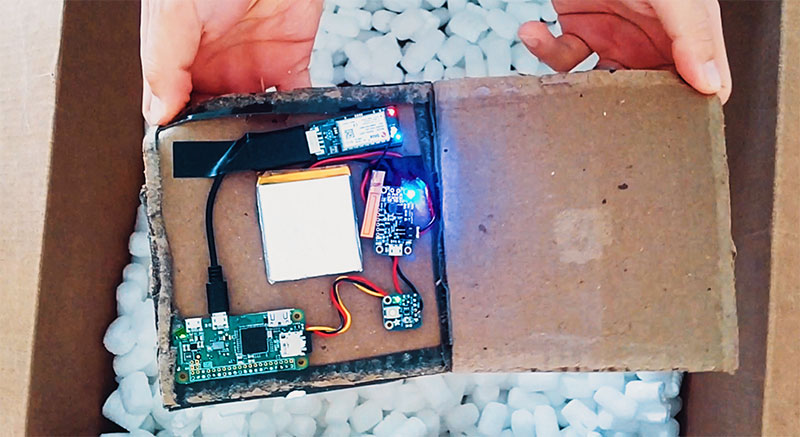
Whilst an attacker needs some technical knowledge to assemble the loose components into the battle package, it’s easy to imagine entrepreneurial criminals soon selling pre-built machines on underground forums. If this were to happen, the threat to businesses would dramatically increase as the attack becomes available to the masses.
Once a battle package is shipped, the modem regularly transmits GPS coordinates to the attacker’s command and control server. This allows the attacker to identify when the device has arrived and start full deployment. Of course, the device doesn’t have to come in the post – it could be planted into a toilet roof or hidden in a bush outside of reception.
Deployment involves one of two things:
- The device will imitate the existing Wi-Fi router, harvesting the login credentials of users who attempt to connect to the rogue access point.
- The device will intercept packets, looking for a handshake (the connection between a device and the Wi-Fi access point). The encoded handshake can then be sent back to the command and control server to be reverse-engineered and used to gain access to the network.
What threat does warshipping pose?
Once the attacker has access to the network, they can exploit vulnerabilities to gain deeper access. This allows for further attacks to be sent directly into the network – eventually creating a persistent backdoor for the attacker. From there, it’s possible for the attacker to gain full access to systems and information.
In business terms, a security breach like this is about as bad as it can get. Hackers would have complete control and access to your IT network and could do anything from deleting days of work with a wiper to a full-scale ransomware attack or even theft of intellectual property and client data. All of these cause massive financial damage to your business alongside making a permanent stain on your reputation.
Warshipping attacks companies from a completely new angle, which allows attackers to bypass nearly all perimeter defences. And with no ‘years proven’ method of mitigation known, the potential threat to businesses is significant.
How to prevent warshipping?
Warshipping bypasses nearly all common perimeter defences by physically intruding into the network. With no proven defences yet, the threat might seem insurmountable, but with some clever planning, it can be pre-emptively mitigated. Your focus should be on securing your wireless access points and effectively handling parcels. There are a few changes you can make now to work towards this:
Upgrade to secure Wi-Fi access points
Upgrading Wi-Fi access points to use Wi-Fi protected access (WPA) at a minimum or WPA2 (an upgraded version of the original standard) can make it difficult for criminals to intercept useful data from your company Wi-Fi due to the use of encrypted traffic.
Even WPA2 will not provide immunity to warshipping though since the standard contains flaws. What WPA2 will do though is require significantly more effort from an attacker – providing additional time to identify and destroy the device.
Prevent employees from delivering packages to the office
By creating a policy that prevents personal packages from being delivered to the office, any unexpected items will be immediately apparent. If preventing personal deliveries is impractical, scanning the contents of a package to identify hidden electronics can be used instead.
Monitor for rogue Wi-Fi devices
Constantly monitoring your company network for new and suspicious devices allows you to identify rogue access points. But technical defences alone are unlikely to remove this risk completely.
Educating employees about the dangers of connecting to lookalike Wi-Fi networks can go a long way in helping them understand what part they play in defending against warshipping.
Establish a quarantine zone for packages
In a company where it’s both infeasible to prevent employees from having packages delivered and to scan for metal or electronic devices in a package (i.e. where hardware is regularly delivered), another method of prevention is isolating the mailroom from the wider network.
Utilise multi-factor authentication
You should already be using multi-factor authentication since it’s a staple of security and something you’d need if you were to operate to a decent IT security framework such as ISO 27001.
Having a second factor means that even if the attacker manages to acquire the password to gain login details, without the second factor, they will still be locked out.
Where does the name ‘warshipping’ come from?
The name warshipping is nothing to do with warships. Instead, it’s derived from shipping (as in package shipping). The name draws from another attack known as wardriving where cyber-criminals will drive around an area, using a similar technique to break into insecure Wi-Fi networks.
What does warshipping tell us about the wider cyber-security landscape?
Warshipping shows us two things about the modern threat landscape. It shows that cyber-criminals are thinking outside the box when it comes to new channels of attack. And it shows a shift away from digital cyber-crime into real-world cyber-crime (a tremendously oxymoronic phrase by the way).
The idea of sending a package containing a hacking device to a company in order to break into the network sounds straight out of the plot of a heist movie. But the fact that we’re now dealing with this as a genuine threat shows the ingenuity of hackers.
If businesses are to keep pace with the new avenues of attack, they need to be dedicating resources to thinking about what the future holds for their cyber-security. If IT teams are already stretched thin, partnering with an IT security provider who will monitor and predict changes in the threat landscape is another option.
As for the shift towards real-world cyber-crime, it’s a trend that’s already been happening. Up to 99% of all cyber-attacks nowadays require human manipulation through social engineering rather than breaking into a network via pure computer skill.
While we’re currently in the era of spear-phishing (meaning spear-phishing is seeing the most widespread success, not necessarily that it’s the most common or newest), as employees become more sceptical of digital communications and wise up on attempts to trick them, criminals will have to transition to real-world approaches. Whether this will take the form of warshipping, USB drop attacks or even face-to-face social engineering, only time will tell.
Despite the constant stories of breaches and cyber-attacks, the tools do exist to counter almost every digital threat. In an environment that follows all security best practices (2FA, zero-trust, patch management, intrusion detection and prevention, e.t.c.) the risks can be controlled to a sensible standard. Most breaches are preventable if the business adheres to the security basics (such as what’s gained through obtaining the Cyber Essentials standard).
The reason we still see successful attacks (outside of companies’ inability to do their due diligence) is because attackers are exploiting humans. With attacks poised to move into the physical realm, not only will many of the digital defences become useless, but the human element will be more vulnerable than ever.

